LAN hardware and software. Local network hardware
Read also
To connect computers in local networks, network adapters (network cards), hubs, switches, and routers are most often used.
Let's take a closer look at each type of equipment.
Network adapter– this is a device necessary to connect a computer to a local network. The network adapter is installed in a free slot (connector) on the computer's motherboard, just like adapters that perform other functions, such as a video adapter. Network adapters can be classified according to the following criteria:
· depending on the type and capacity of the internal bus used in the computer;
· depending on the type accepted in the network network technology– Ethernet, Token Ring, FDDI, etc.;
· depending on the type of data transmission medium (channel) - coaxial cable, fiber optic cable, twisted pair cable.
The network adapter is connected to the cable using special connectors. For a twisted pair cable, an RG-45 connector is used, which looks like a telephone connector. To connect to a coaxial cable, so-called BNC connectors and T connectors are used. There are network adapters that use wireless principle interactions. Currently, the three main types wireless transmission data are radio communications, microwave communications and infrared communications. Currently, the most common option for organizing a wireless local network is the use of WiFi equipment. WiFi is an acronym for "Wireless Fidelity" ( wireless connection) and represents the standard wireless access, providing information transfer speeds of up to 54 Mbit/s.
Each network adapter has a unique internal number, the so-called MAC address, which allows you to uniquely identify the source of information in the network environment.
Various types cables used as carriers or data transmission media. Although wireless data transmission technologies are becoming increasingly popular nowadays, the main type of media for network communications the cable remains. The most common cable types are:
· twisted pair cable;
· coaxial cable;
· fiber optic cable.
Twisted pair cable– the most common type of cable at present, there are two types: unshielded and shielded twisted pair. The internal structure consists of several twisted pairs copper wires, surrounded by a grounded sheath of copper mesh, or aluminum foil in the case of shielded twisted pair cables. There are several types of unshielded twisted pair cable. Currently, the most commonly used type is UTP-5 (UTP - Unshielded Twisted Pair). The UTP-5 cable provides information transfer speeds of up to 1000 Mbit/s. Unshielded twisted pair cable is the cheapest and easiest type of cable to install. But it also has disadvantages. The cable is sensitive to interference from external electromagnetic sources and interference of signals between the individual wires of the cable itself. Length of the cable segment, i.e. the distance from the computer to the signal amplifier (repeater) cannot exceed 100 meters, since the signal weakens as it moves along the cable.
Shielded twisted pair cable (STP – Shielded Twisted Pair) is less susceptible to external electromagnetic influences and is more difficult to install. The length of the cable segment is also limited to 100 meters.
Coaxial cable resembles the cable that is used to connect an antenna to a household television. The data transfer rate for this type of media is 10 Mbit/s. The length of the cable segment can range from 185 to 500 m, depending on the type of coaxial cable. The most widely used are the so-called “thin” cable markings RG-58 and “thick” cable markings RG-8 and RG-11. This type of cable is obsolete and is little used nowadays.
Fiber optic cable is currently the most advanced, but also the most expensive medium for transmitting information. The optical fiber is made of quartz, which is based on silicon dioxide. The cable consists of a central fiber conductor through which the light signal travels, surrounded by another layer of fiber. The refractive index of a light beam is different for these two layers. There are two types of cables: single-mode, in which only one beam can propagate, and multimode, in which many beams can propagate. In single-mode fiber, the diameter of the central fiber conductor is slightly smaller than in multimode fiber. Information transfer speed when used of this type cable reaches 10 Gb/s (10000 Mbit/s). Fiber optic cable is used mainly in global and regional networks, as well as on the backbones of large local networks.
Hub(multiport repeater, or HUB) is a device used to connect individual workstations (computers) into a local network. Modern hubs usually have 8, 12, 16, 24, or 48 ports (connectors) for connecting computers. All hub ports are equal. When a signal is received from one of the computers connected to it, the hub broadcasts it to all other ports. Thus, a hub is the central point of connection between computers on a network. In addition to the function of connecting computers, the hub can perform several other functions. These are: signal amplification (repetition), auto-segmentation ( automatic shutdown faulty ports), ensuring the collection of statistics on network load. Hubs can be connected to each other to increase the size of the network.
Switch(switch) is a device that can also be used to connect computers, or different segments of a local network (LAN). Unlike a hub, a switch, when receiving a signal (data packet) from one of the computers connected to it, does not broadcast it to all other ports, but transmits it only to the port to which the computer that is the recipient of this data packet is connected. As a result, the data transfer speed increases, since the number of collisions characteristic of the network is reduced. Ethernet technologies.
LPs tend to outgrow initial projects. As companies grow, so do drugs. A change in the business profile or organization of a company's work may require network reconfiguration. This becomes obvious when:
- Documents wait in line for a network printer for an unacceptably long time;
- database query time increased;
- information protection requirements have changed, etc.
Networks cannot expand by simply adding workstations and laying cables. Any topology or architecture has its limitations. However, there are devices that can:
- segment the drug so that each segment becomes an independent drug;
- combine two drugs into one;
- connect LANs to other networks to connect them to the Internet.
Such devices include: repeaters, bridges, routers, bridge routers and gateways.
Repeaters
These are devices that receive a fading signal from one network segment, restore it and transmit it to the next segment, thereby increasing the range of signal transmission between individual network nodes (Fig. below).
Connecting a repeater to a LAN
Repeaters transmit all traffic in both directions and operate on physical level OSI models. This means that each segment must use the same packet formats, protocols, and access methods. That is, with the help of a repeater you can combine single network two Ethernet segments and impossible Ethernet and Token Ring.
However, repeaters make it possible to connect two segments that use different physical signal transmission media (cable - optics, cable - pair, etc.). Some multiport repeaters act as multiport hubs, connecting different types of cables.
The use of repeaters is justified in cases where it is necessary to overcome the limitation on the length of the segment or the number of PCs. Moreover, none of the network segments generates increased traffic, and the cost of the LAN is the main factor. This is due to the fact that repeaters do not perform the functions of isolation and filtration.
Thus, transmitting every bit of data from segment to segment, they will transmit both corrupted packets and packets not intended for this segment. As a result, the problems of one segment will affect others. Those. The use of repeaters does not provide the segment isolation function. In addition, repeaters will distribute all broadcast packets throughout the network. And if a device does not respond to all packets, or packets are constantly trying to reach devices that never respond, then network performance drops, i.e., repeaters do not filter signals.
Bridges
A bridge is a device that connects two networks that use the same data transfer methods. These devices, like repeaters, can:
- increase the size of the network and the number of PCs in it;
- connect dissimilar network cables. However, their fundamental difference is that they operate at the data link level of the OSI model, i.e. at a higher level than repeaters and take into account more features of the transmitted data, allowing:
- restore the shape of signals, but doing it at the packet level;
- connect dissimilar network segments (for example, Ethernet and Token Ring) and transfer packets between them;
- improve the performance, efficiency, security and reliability of networks (which will be discussed below).
Operating principles of bridges
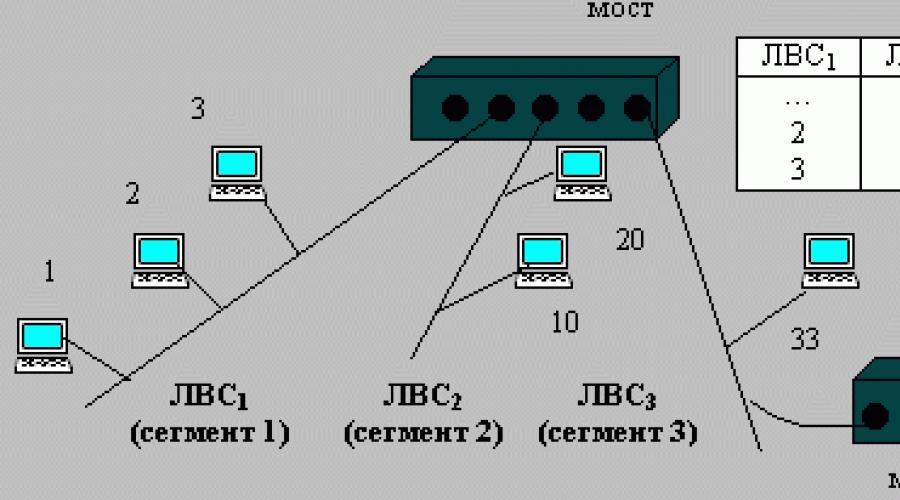
The operation of the bridge is based on the principle that all network nodes have unique network addresses, and the bridge transmits packets based on the address of the destination node (Fig. below).

An example of integrating LAN segments using bridges
When controlling access to the network, the bridge:
- listens to all traffic;
- checks the source and destination addresses of the packet;
- builds a routing table;
- transmits packets based on the destination host address.
The bridge has some "intelligence" because it learns where to send the data. When packets are sent across a bridge, the transmitter addresses are stored in the bridge's memory and a routing table is created based on them. At the start of work, the table is empty. Then, when nodes transmit packets, their addresses are copied into the table. With this data, the bridge studies the location of computers on network segments. Listening to the traffic of all segments and receiving the packet, the bridge looks for the transmitter address in the routing table. If the source address is not found, it adds it to the table. Then it compares the recipient address with the routing table database.
- If the destination address is in the table and the destination is in the same segment as the source, the packet is discarded. This filtering reduces network traffic and isolates network segments.
- If the destination address is in the table, but the destination and source are on different segments, the bridge forwards the packet through the appropriate port to the desired segment.
- If the address is not in the table, the packet is relayed to all segments, excluding the one from which it was received.
In short, if the bridge knows the location of the destination node, it forwards the packet to it. Otherwise, it broadcasts the packet to all segments.
The considered option corresponds to the simplest, so-called transparent bridges. Currently, bridges with a spanning tree algorithm, bridges with source routing, etc. are used.
Purpose of bridges
- Bridges allow you to increase the coverage range of your network by working as repeaters. In this case, a cascaded LAN connection via bridges is allowed. Moreover, these LANs can be heterogeneous.
- The use of bridges improves network performance due to the possibility of network segmentation. Since bridges are able to filter packets according to certain criteria, a large network is divided into several segments connected by bridges. Two small segments will work faster than one large one because traffic is localized within each segment.
- The use of bridges increases the efficiency of the network, because for each subnet (segment) you can use different topologies and transmission media, and then connect them with bridges. So, for example, if in individual departments the PCs are connected by twisted pairs, then these subnets can be bridged to the corporate LAN with an optical backbone. Since twisted pair cables are cheap, this will save money, and the core backbone (which carries most of the traffic) will use a high-bandwidth environment.
- Bridges allow you to increase the security (protection) of data due to the fact that they can be programmed to transmit only those packets that contain the addresses of specific senders and recipients. This allows you to limit the circle of PCs capable of sending and receiving information from another subnet. For example, in a network serving accounting, you can install a bridge that will allow only some external stations to receive information.
- Bridges increase the reliability and resiliency of the network. With network segmentation, the failure of any subnet will not cause all others to fail. In addition, when a single file server goes down, the entire network stops working. If, using internal bridges, you connect two file servers that protect each other, then:
- network fault tolerance will increase;
- traffic levels will decrease.
There are local and remote bridges. Remote bridges are used in large networks when its individual segments are connected by telephone (or other) communication channels.
However, if only one local bridge is used to connect two cable LAN segments, then in large networks it is necessary to use two remote bridges connected via synchronous modems to a dedicated communication channel (Fig. below).

Using two remote bridges
Routers
A router is a device for connecting networks using different architectures and protocols. Working at the network layer of the OSI model, they can:
- switch and route packets across multiple networks;
- determine the best route for their transmission;
- bypass slow and faulty channels;
- filter broadcast messages;
- act as a security barrier between networks.
A router, unlike a bridge, has its own address and is used as an intermediate destination.
LAN hardware components: workstations, servers, interface cards and cables.
Workstations (PCs) – personal computers, - workplaces of network users. Sometimes PCs may not have hard drives. Such workstations are called diskless PCs. Their advantage is low cost, high security against penetration into the system by unauthorized persons and computer viruses; disadvantage - there is no possibility to work offline, to have your own archives of data and programs.
Servers on the LAN perform the functions of distributing network resources. The server is quite powerful Personal Computer, minicomputer or special computer server. There can be several servers on one network. A personal computer server can combine the functions of a server and workstation. The collection of server computers and server-related workstations is called a domain.
The network adapters used in a LAN have three main characteristics: the type of computer bus to which they are connected (ISA, EISA, Micro Channel, etc.), the bit width (8, 16, 32, 64) and the method used to access network channel data.
The main schemes for connecting computers to a LAN are: “star”, “ring” and “common bus”.
Widely used network channel access methods:
o Ethernet (supports bus topology);
o Arcnet (supports star topology);
o Token-Ring (supports ring topology).
In the classification of LAN topologies, there are two main classes: broadcast and serial.
In broadcast configurations, each personal computer transmits signals that can be received by other computers. These configurations include bus, tree, and star topologies.
In sequential configurations, each physical sublayer transmits information to one computer. Examples: random (random connection of computers), hierarchical, “ring”, “chain”, “star with an intellectual center”, “snowflake”.
To connect computers on a LAN, coaxial (thin and thick) cables, twisted pair cables and optical fiber are used, and work is underway to introduce wireless radio networks.
Optional equipment LAN - sources uninterruptible power supply, modems, transceivers, repeaters and connectors (connectors, terminators).
Management principles
There are two main principles of management in a LAN: centralized and decentralized. In centralized networks there is a central node (server computer (CS)) and workstations.
The main purpose of a server computer is to manage data transfer on a network and store files used by many workstations. Server computers are usually connected to laser printers, faxes, modems, scanners, etc.
Network OS, implementing centralized control: Microsoft Windows NT Server, Novell NetWare (versions 3.X and 4.X) and others.
The advantages of centralized networks: high security of network resources from unauthorized access, ease of network administration, the ability to create networks with a large number of nodes.
Disadvantages: vulnerability of the system when the file server malfunctions, as well as high demands on server resources.
Networks with decentralized management (peer-to-peer networks) do not contain a server computer. Network management functions are transferred one by one from one workstation to another. The core resources of all workstations are usually publicly available. Peer-to-peer networks are built on the following programs and packages: Novell NetWare Lite, Windows for Workgroups, Windows95/98 and others.
Deploying a peer-to-peer network across a small number of workstations allows for a more efficient and resilient distributed computing environment. Network software is simpler compared to centralized networks. However, such networks are weaker in terms of information security and administration.
A resource consumer on the network is called client , and the resource-providing network component is server . The main types of resources: hardware (entire computer, disk drive, printing device, etc.), software and information. Typical network clients are: a computer, a user or a program. For a hardware resource, the terms used are disk server (file server or file server). Processing of incoming messages is performed by message servers, processing of database requests by database servers, and execution of user applications by application servers. Sometimes the same term refers to different (hardware and hardware-software) components of a computer system. For example, a print server is a computer with a printer connected to it, a printing program, or a computer with print management software.
Subject
- Network hardware and software.
Target
- Introduce devices and software, with the help of which a computer network is created.
During the classes
To create and operate computer networks special devices and software are required. Network hardware includes network adapter, network cable, modem, router and main computer – these devices allow you to organize a local network and the ability to access Internet.
Host
Main technical device is special computer, providing information functions. Such a machine is called a host computer - it must always be on, as it ensures reception and data transfer over the network.
All other computers must be connected to the host machine in one way or another. After all, every user working within the network uses its resources under any circumstances.
Using Ethernet, the machines are connected to each other. Such a system consists of elements such as cable (twisted pair), special connectors and network adapters. The cable is used when transmitting and receiving information between workstations.

To connect the cable, connectors are used that connect through T-connectors to network adapters - special network cards. They can be integrated or inserted into the expansion slots of the computer motherboard.
Routers needed to connect to open ends of the network.
Cables are used for Ethernet equipment different types. These include coaxial cables (coaxial cables) and twisted pair cables. Each type of cable requires a different connector and its own way of connecting to the network card. But it should be noted that the coaxial connection type is no longer used in many places due to its slow speed and unreliable connection. Depending on the cable, the characteristics of the network change - the length of the cable and the maximum number of workstations connected to it.

The data transfer speed in the Ethernet network is about 100 Mbit/second.
To connect a computer to telephone network(through which the connection to the Global Network occurs), you must have a special device - modem (MO dulator – DEM odulator).

Modulation is the process of converting digital form of information transmission into analogue.
Demodulation– inverse transformation for receiving information. Modems can be external or internal. An external modem is a separate device connected to a PC via a COM port (every computer has one), while an internal modem is an electronic board that can be purchased separately and installed inside the system unit.
One of important characteristics The modem has a data transfer rate (Kbit/sec). Old modems have a connection speed of 36 Kbps, but modern ones have a higher speed - 128 - 256 Kbps, etc.
Network adapter
The network card is a separate board that is inserted into the motherboard PC. It, like many other devices, can be integrated into the motherboard. Network adapters are data reception/transmission devices and are designed to connect workstations not only to each other, but also between the host computer and the router to access Internet.
Network software
TO |software network functioning includes such components as network operating systems network applications (browsers, etc.).
Network operating system
Network operating system- This is the basis of any network. It is necessary to manage received/transmitted messages between servers and workstations. It also allows any user to work with a common network drive or a printer that are not physically connected to this computer. The most popular, practical and simply popular are network operating systems such as Unix and Microsoft Windows Server 2003 and 2008.

In a network operating system installed on a separate PC, the following characteristics can be distinguished:
- PC resource management (distribution random access memory, peripheral device management and other functions
- provision of own resources for general use(sharing)
- means by which messages are exchanged and transmitted on the network.
Depending on the functions of the computer itself, its operating system may contain either a client or a server part.

Browser Browser) – network software designed to display the content of web pages written in special web languages.

Browsers are also used to download and upload various content to the World Wide Web.
Questions
1. What is the network maintenance hardware?
2. What is a network adapter for?
3. What is a modem?
4. What functions does the network OS perform?
5. Tell us about browsers.
List of sources used
1. Lesson on the topic: “Operation computer networks", Igolkin A.P., Makeevka.
2. Morgunov Zh. Ts. Modern computer networks. – 2008
Edited and sent by a teacher at Kyiv National University. Taras Shevchenko Solovyov M. S.
We worked on the lesson
Soloviev M. S.
Igolkin A.P.
Send your good work in the knowledge base is simple. Use the form below
Students, graduate students, young scientists who use the knowledge base in their studies and work will be very grateful to you.
Posted on http://www.allbest.ru/
Ministry of Agriculture of the Russian Federation
State Agrarian University of the Northern Trans-Urals
Institute of Economics and Finance
Department of Economic and Mathematical Methods and computer technology
on topic: LAN HARDWARE
Head Eremina D.V.
Performer Rodkin M.A.
Tyumen 2014
- Introduction
- 1. Local network equipment
- 2. Types of local networks
- 3. Local network topologies
- Conclusion
- List of used literature
Introduction
The transfer of information between computers has probably existed since the very beginning of computer technology. It allows you to organize working together separate computers, solve one problem using several computers, specialize each computer to perform one function, share resources and solve many other problems. Recently, many methods and means of exchanging information have been proposed: from the simplest transfer of files using a floppy disk to worldwide computer Internet networks, capable of connecting all the computers in the world. What place in this entire hierarchy is given to local networks? Undoubtedly a big one. Most often, the term “local area networks” (LAN, Local Area Network) is taken literally, that is, local refers to networks that are small, local in size, and connect nearby computers. But how do computers connect?
computer local network packet
1. Local network equipment
In order for data transfer over a local network to take place, the following components are required:
1. Cables for information transmission - networks on the territory of one facility, purpose - providing technological and production communications within the facility. Example - local cable lines between buildings in the city ( different enterprises) or nearby settlements (towns, villages...), purpose - providing communications at the local level, for example, channels telephone communication to connect a departmental PBX to a city PBX. Intrazonal - cable lines within one edge, area, purpose - providing communications within a given zone. Trunk lines are cable lines passing (connecting) more than one entity, the purpose of which is to provide communication between entities. international - cable lines passing across the border of a state(s), purpose - providing communications between countries (Internet).
Figure 1. Cables for transmitting information
2. Connectors for connecting cables - (Registered jack RJ, read “ar-jay”) is a standardized physical interface used to connect telecommunications equipment. The standard versions of this connector are called RJ11, RJ14, RJ25, RJ45, and so on. RJ connectors belong to the modular connector family, with the exception of RJ21. For example, RJ11 uses a modular plug and socket type "6 pins - 2 conductors".
3. Matching terminators - an energy absorber (usually a resistor) at the end of a long line, the resistance of which is equal to the characteristic impedance of this line. The word "terminator" is used mainly in computer jargon; a terminological synonym for it is the expression "matched load"
4. Network adapters are peripheral devices that allow the computer to interact with other network devices.
Figure 2. Network adapters
5. Repeaters - designed to increase the distance of a network connection by repeating electrical signal"one to one." There are single-port repeaters and multi-port repeaters. In terms of the OSI model, it operates at the physical layer.
Figure 3. Repeaters
6. Transceivers are a device for transmitting and receiving a signal between two physically different media of a communication system. This is a receiver-transmitter, physical device, which connects the host interface to a local network such as Ethernet. Ethernet transceivers contain electronic devices, transmitting a signal to the cable and detecting collisions
7. Hubs are a network device designed to combine several Ethernet devices into a common network segment. Devices are connected using twisted pair, coaxial cable or optical fiber.
Figure 4. Hubs
8. Bridges: Northbridge (in some cases Intel chipsets, also - memory controller-hub English. Memory Controller Hub (MCH) -- system chipset controller on motherboard x86 platform, to which, as part of the organization of interaction, they are connected: through the Front Side Bus - a microprocessor, if the processor does not have a memory controller, then through the memory controller bus - RAM, through the graphics controller bus - a video adapter (in motherboards of the lower price range video adapter is often built-in). In this case, the northbridge made by Intel is called GMCH (from English Chipset Graphics and Memory Controller Hub). The name can be explained by the representation of the chipset architecture in the form of a card. As a result, the processor will be located at the top of the map, in the north. Based on the purpose, the north bridge determines the parameters (possible type, frequency, throughput) system bus and, indirectly, the processor (based on this - to what extent the computer can be overclocked), RAM (type - for example SDRAM, DDR, its maximum capacity), connected video adapter.
9. Bridges: Southbridge (functional controller), also known as I/O Controller Hub (ICH). Typically this is a single chip that connects “slow” (compared to the CPU-RAM coupling) interactions (for example, Low Pin Count, Super I/O or bus connectors for connecting peripheral devices) on the motherboard to the CPU via the Northbridge , which, unlike Yuzhny, is usually connected directly to the central processor.
10. Routers - specialized network computers, having at least two network interfaces, and forwarding data packets between different network segments, making forwarding decisions based on information about the network topology and certain rules set by the administrator.
11. Gateways -- network devices or software tool for interconnecting heterogeneous networks. Internet gateway is a program or equipment that organizes access from a local network to the Internet. The default gateway is the address of the router to which traffic for which a route cannot be determined based on routing tables is sent.
Also, special network software is required to work on a local network. The Windows operating system already has everything you need to set up a network.
And so, having all the software components, you can organize the work of a local network to solve some problems. For example, file sharing, file transfer and others.
2. Types of local networks
Peer-to-peer local network:
In small local networks, all computers are usually equal, i.e. users independently decide which resources of their computer to make publicly available. Such networks are called peer-to-peer.
A peer-to-peer local network is a network that supports equal rights between computers and allows users to independently decide which resources of their computer: folders, files, programs to make publicly available.
Figure 5. Peer-to-peer local network
Server based local network:
If there are more than 10 computers connected to the local network, the peer-to-peer network may not perform well enough. To increase productivity, as well as to ensure greater reliability when storing information on the network, some computers are specifically dedicated to storing files or application programs. Such computers are called servers, and a local area network is called a server-based network.
Server is a special control computer designed for:
1. Data storage for the entire network.
2. connecting peripheral devices;
3. centralized management of the entire network;
4. determination of message transmission routes.
Figure 6. Server-based network
3. Local network topologies
Local network topology (structure) - network configuration, order of connecting computers on the network and appearance networks.
Using a local network cable, each computer connects to other computers. The structure of a local network can be described using a network information model.
Bus (linear bus) is a variant of connecting computers to each other, when a cable runs from one computer to another, connecting the computers in series with each other.
Figure 7. Bus LAN
Star - each workstation is connected to a separate cable from one node - the server. The server provides centralized management of the entire network, determines message transmission routes, connects peripheral devices, and is a data repository for the entire network.
Figure 8. Star local network
Ring - all computers are connected in a ring, and the server functions are distributed among all machines on the network. Disadvantage: if any computer fails, the network operation is interrupted.
Figure 9. Ring LAN
Tree-like (snowflake) - allows you to structure the system in accordance with the functional purpose of the elements. The most flexible structure. Almost all complex systems contain hierarchical structures.
Figure 10. Tree local network
4. Network protocol. Packet protocol
The operation of computers on a local network is controlled by programs. In order for all computers to understand each other, send each other requests and receive responses, they must communicate in the same language. This language of communication between computers is called a network protocol.
Last time wide application found so-called packet protocols. When using this type of protocol, the data exchanged between computers is cut into small blocks. Each block is, as it were, put into an “envelope” (encapsulated), resulting in a package. The packet contains both the data itself and service information: from whom it was sent, to whom it is intended, which packet should follow it, etc. The packet protocol ensures the circulation of packets in the network, as well as their receipt by the addressee and assembly. Each workstation periodically connects to the network (via interrupts) and checks passing packets. She takes the ones addressed to her, and forwards the others on.
Let's look at a simple example of packet communication. Let's say we wrote a letter to a friend on three sheets of paper, then we put them in three envelopes, put the numbers 1, 2, 3 on them and put them in three different mailboxes. Each piece of paper will go its own way to the addressee. It is possible that the third piece of paper will arrive before the first, but this will not prevent you from collecting them in the correct order and reading them. In any correspondence special role plays an envelope - a necessary element of the protocol established by the postal service. The envelope states where the contents should be delivered (recipient's address and zip code) and indicates where the envelope should be returned in case of non-delivery (return address). If the envelope is signed incorrectly or does not have a stamp on it indicating that the service has been paid for, then the protocol is not followed and the letter may not reach the addressee.
Figure 11. Packet circulation
Thus, the functioning of any local network is based on the following principles:
Each of the machines included in the network has its own number (identifier);
Information from each machine enters the network in the form of separate portions (packets);
The package is supplied with information about which machine it is intended for;
The packet moves freely across the network, and this part of the information is compared with the identifier of each computer and, if there is a match, the message is sent to the corresponding machine.
Conclusion
In conclusion, we can say that modern technologies are developing at a very fast pace. Local networks, the Internet has taken a very important place, it is difficult to imagine an ordinary plant that will not have computers connected via a network. In modern conditions this is simply not possible.
Many ways and opportunities have emerged to connect computers to perform different purposes, this greatly simplifies human activities.
Almost every day new components of local networks appear, surpassing the previous ones in their performance. Data transfer speeds can exceed 100, 200, and even 500 MB.
In general, the entire process of network development has had a positive impact on the development of technology and provided enormous opportunities for people to communicate. And, most likely, modern networks will continue to improve.
List of used literature
1. Local network [Electronic resource] - http://www.authorstream.com - (access date: 12/16/2014)
2. Local network. What is this? Types of local networks [Electronic resource] - http://pro-spo.ru/network-tech - (date of access: 16.1.2014)
3. Free encyclopedia [Electronic resource] - http://ru.wikipedia.org - (access date: 12/16/2014)
Posted on Allbest.ru
Similar documents
Wireless technology transmission of information. Development of wireless local networks. WEP security standard. WEP encryption procedure. Breaking wireless network. Hidden network ID mode. Authentication types and protocols. Hacking a wireless network.
abstract, added 12/17/2010
Computer switching methods. Classification, structure, types and principles of constructing local computer networks. Selecting a cable system. Features of the Internet and other global networks. Description of the main data exchange protocols and their characteristics.
thesis, added 06/16/2015
The concept and structure of computer networks, their classification and varieties. Technologies used to build local networks. Security of wired local networks. Wireless local networks, their characteristic properties and devices used.
course work, added 01/01/2011
Organization of a private network. The structure of an unprotected network and types of threats to information. Typical remote and local attacks, mechanisms for their implementation. Selecting security tools for the network. Scheme of a secure network with a Proxy server and coordinator within local networks.
course work, added 06/23/2011
Characteristics of the features of local, regional and global computer networks. Examples of network integration. Studying the classification of networks between nodes. Fiber optic cables. Communication channel capacity. Information transfer speed.
presentation, added 10/30/2016
Analysis of educational and methodological literature. Modeling a system of symbolic teaching aids. Topology of computer networks. Rules of network interaction. Twisted pair cables. Construction of thematic control means. Local network equipment.
course work, added 06/07/2016
Computer networks and their classification. Computer network hardware and local network topologies. Technologies and protocols of computer networks. Addressing computers on the network and basic network protocols. Advantages of using network technologies.
course work, added 04/22/2012
Features, differences, topology and functioning of local computer networks. Software for information and computer networks. Basic data transfer protocols, their installation and configuration. Authentication and authorization; Kerberos system.
course work, added 07/20/2015
Basic technologies, protocols and standards for building local and global networks. Data transmission protocols in telecommunication systems. Communication protocol stacks, communication lines, cable standards, coaxial and fiber optic cables.
course work, added 07/15/2012
Analysis of a system of distributed local networks and information exchange between them via the Internet. Distinctive features corporate network, problem identification information security in the Internet. The technology for building a virtual secure network is VPN.
Local area network is a concept that is familiar to many firsthand. Almost every enterprise uses this technology, so it can be said that every person has come across it in one way or another. Local networks have significantly accelerated production processes, thereby giving a sharp boost to their further use throughout the globe. All this allows us to predict further growth and development similar system data transfer, up to the implementation of a LAN in every, even the smallest enterprise.
The concept of a local network
A local area network is a number of computers connected to each other by special equipment that allows for the full exchange of information between them. Important feature This type of data transmission is a relatively small area where communication nodes are located, that is, the computers themselves.
Local networks not only greatly facilitate interaction between users, but also perform some other functions:
- Simplify work with documentation. Employees can edit and view files at their workplace. At the same time, there is no need for collective meetings and meetings, which saves valuable time.
- They allow you to work on documents together with colleagues, when everyone is at their own computer.
- They allow access to applications installed on the server, which allows you to save free space on the installed hard drive.
- Save hard drive space by allowing you to save documents on your host computer.
Types of networks
A local area network can be represented by two models: a peer-to-peer network and a hierarchical one. They differ in the ways communication nodes interact.
A peer-to-peer network is based on the equality of all machines, and data is distributed between each of them. Essentially, a user of one computer can access the resources and information of another. The efficiency of the peer-to-peer model directly depends on the number of worker nodes, and its level of security is unsatisfactory, which, coupled with a rather complex management process, makes such networks not very reliable and convenient.

The hierarchical model includes one (or more) main server, where all data is stored and processed, and several client nodes. This type of network is used much more often than the first, having the advantage of speed, reliability and security. However, the speed of such a LAN largely depends on the server, which under certain conditions can be considered a disadvantage.
Drawing up technical requirements
Designing a local area network is a rather complex process. It begins with the development of a technical specification, which should be carefully considered, since shortcomings in it threaten subsequent difficulties in building a network and additional financial costs. Primary design can be done using special configurators that will allow you to select the optimal network equipment. Such programs are especially convenient because they can be corrected different meanings and parameters directly during operation, as well as generate a report at the end of the process. Only after these steps can you proceed to the next stage.
Schematic design
This stage consists of collecting data about the enterprise where it is planned to install a local area network, and analyzing the information received. The quantity is determined:
- Users.
- Workstations.
- Server rooms.
- Connection ports.

An important point is the availability of data on the routes for laying highways and the planning of a specific topology. In general, it is necessary to adhere to a number of requirements imposed by the IEEE 802.3 standard. However, despite these rules, sometimes it may be necessary to make calculations of signal propagation delays or consult with network equipment manufacturers.
Basic LAN characteristics
When choosing a method for placing communication nodes, you must remember the basic requirements for local networks:
- Performance, which combines several concepts: throughput, response time, transmission delay.
- Compatibility, i.e. ability to connect various local area network equipment and software.
- Safety, reliability, i.e. capabilities to prevent unauthorized access and complete data protection.
- Scalability - the ability to increase the number of workstations without degrading network performance.
- Manageability - the ability to control the main elements of the network, prevent and eliminate problems.
- Network transparency, which consists of presenting a single computing device to users.
Basic local area network topologies: advantages and disadvantages
The topology of a network represents its physical layout, significantly affecting its basic characteristics. In modern enterprises, three types of topologies are mainly used: “Star”, “Bus” and “Ring”.

The “Star” topology is the most common and has many advantages over others. This installation method is highly reliable; If any computer fails (except the server), this will not affect the operation of the others.
The “Bus” topology is a single backbone cable with connected computers. Such an organization of a local area network saves money, but is not suitable for unification large quantity computers.
The “Ring” topology is characterized by low reliability due to the special arrangement of nodes - each of them is connected to two others using network cards. The failure of one computer leads to the shutdown of the entire network, so this type of topology is used less and less.
Detailed network design
An enterprise local area network also includes various technologies, equipment and cables. Therefore, the next step will be the selection of all these elements. Making a decision in favor of one or another software or hardware is determined by the purpose of creating the network, the number of users, the list of programs used, the size of the network, and its location. Currently, fiber optic highways are most often used, which are distinguished by their high reliability, speed and availability.
About cable types
Cables are used in networks to transmit signals between workstations; each of them has its own characteristics, which must be taken into account when designing a LAN.

- A twisted pair consists of several pairs of conductors covered with insulation and twisted together. Low price and ease of installation are advantageous benefits, which makes this cable the most popular for installing local networks.
- A coaxial cable consists of two conductors inserted one inside the other. A local area network using coax is no longer so common - it was replaced by twisted pair, but it is still found in some places.
- Optical fiber is a glass thread that can carry light by reflecting it off walls. A cable made from this material transmits data over long distances and is fast compared to twisted pair and coaxial cables, but it is not cheap.
Necessary equipment
Network equipment of local area networks includes many elements, the most commonly used of which are:

- Hub or hub. It connects a number of devices into one segment using a cable.
- Switch. Uses special processors for each port, processing packets separately from other ports, due to which they have high performance.
- Router. This is a device that makes decisions about sending packets based on data about routing tables and some rules.
- Modem. Widely used in communication systems, providing contact with other workstations via a cable or telephone network.
End network equipment
Hardware local area network necessarily includes server and client parts.
The server is powerful computer, having high network significance. Its functions include storing information, databases, serving users and processing program codes. The servers are located in special rooms with a controlled constant air temperature - server rooms, and their housing is equipped with additional protection from dust, accidental shutdown, as well as a powerful cooling system. As a rule, only system administrators or company managers.

A workstation is a regular computer connected to a network, that is, it is any computer that requests services from the main server. To ensure communication at such nodes, a modem is used and network card. Since workstations usually use server resources, the client part is equipped with weak memory sticks and small hard drives.
Software
Local area network equipment will not be able to fully perform its functions without suitable software. The software part includes:
- Network operating systems on servers that form the basis of any network. It is the OS that controls access to all network resources, coordinates packet routing, resolves device conflicts. Such systems have built-in support for the TCP/IP, NetBEUI, IPX/SPX protocols.
- Autonomous operating systems that manage the client side. They are common operating systems, for example, Windows XP, Windows 7.
- Network services and applications. These software elements allow you to perform various actions: viewing remote documentation, printing on a network printer, sending email messages. Traditional services HTTP, POP-3, SMTP, FTP and Telnet are the basis of this category and are implemented using software.
Nuances of designing local networks
Designing a local area network requires a long and leisurely analysis, as well as taking into account all the subtleties. It is important to provide for the possibility of enterprise growth, which will entail an increase in the scale of the local network. The project must be drawn up in such a way that the LAN is ready at any time to connect a new workstation or other device, as well as upgrade any of its nodes and components.
Security issues are no less important. The cables used to build the network must be reliably protected from unauthorized access, and the lines must be located away from potentially dangerous places where they can be damaged - accidentally or intentionally. LAN components located outside the premises must be grounded and securely secured.
Developing a local area network is a fairly labor-intensive process, but with the right approach and due responsibility, the LAN will operate reliably and stably, ensuring uninterrupted user experience.