Fundamentals of information security. Chapter V
Read also
Software and hardware means of protection against unauthorized access include measures of identification, authentication and access control to the information system.
Identification is the assignment of unique identifiers to access subjects.
This includes radio frequency tags, biometric technologies, magnetic cards, universal magnetic keys, logins for entering the system, etc.
Authentication - verification of the ownership of the access subject to the presented identifier and confirmation of its authenticity.
Authentication procedures include passwords, pin codes, smart cards, usb keys, digital signatures, session keys, etc. The procedural part of the means of identification and authentication is interconnected and, in fact, represents the basic basis of all software and hardware tools for ensuring information security, since all other services are designed to serve specific subjects correctly recognized by the information system. IN general view identification allows the subject to identify himself to the information system, and with the help of authentication, the information system confirms that the subject is really who he claims to be. Based on the passage of this operation, an operation is performed to provide access to the information system. Access control procedures allow authorized entities to perform actions permitted by the regulations, and the information system to control these actions for the correctness and correctness of the result obtained. Access control allows the system to hide from users data to which they do not have access.
The next means of software and hardware protection is logging and auditing of information.
Logging includes the collection, accumulation and storage of information about events, actions, results that took place during the operation of the information system, individual users, processes and all software and hardware that are part of the enterprise information system.
Since each component of the information system has a predetermined set of possible events in accordance with the programmed classifiers, the events, actions and results are divided into:
- external, caused by the actions of other components,
- internal, caused by the actions of the component itself,
- client, caused by the actions of users and administrators.
Information audit consists in carrying out operational analysis in real time or in a given period.
Based on the results of the analysis, either a report is generated on the events that have taken place, or an automatic response to an emergency situation is initiated.
The implementation of logging and auditing solves the following tasks:
- ensuring accountability of users and administrators;
- enabling the reconstruction of the sequence of events;
- detection of attempts to violate information security;
- providing information to identify and analyze problems.
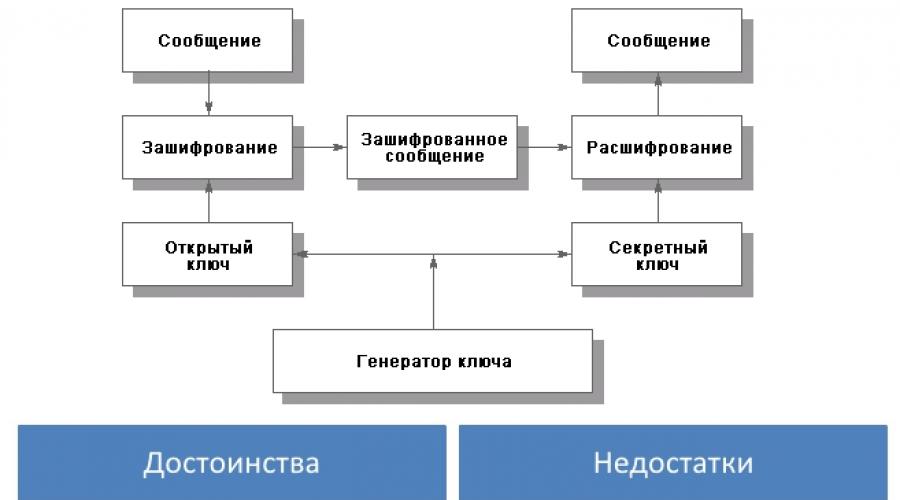
Often, information protection is impossible without the use of cryptographic means. They are used to provide encryption, integrity and authentication services when the means of authentication are stored in encrypted form by the user. There are two main encryption methods: symmetric and asymmetric.

Integrity control allows you to establish the authenticity and identity of an object, which is a data array, individual portions of data, a data source, and also to ensure the impossibility of marking the action performed in the system with an array of information. The implementation of integrity control is based on data conversion technologies using encryption and digital certificates.
Another important aspect is the use of shielding, a technology that allows, by delimiting the access of subjects to information resources, to control all information flows between the enterprise information system and external objects, data arrays, subjects and counter-subjects. Flow control consists in filtering them and, if necessary, transforming the transmitted information.
The task of shielding is to protect internal information from potentially hostile external factors and actors. The main form of shielding implementation is firewalls or firewalls, of various types and architectures.
Since one of the signs of information security is the availability of information resources, ensuring a high level of availability is an important direction in the implementation of software and hardware measures. In particular, two areas are divided: ensuring fault tolerance, i.e. failover of the system, the ability to work when errors occur, and the provision of safe and fast recovery from failures, i.e. serviceability of the system.
The main requirement for information systems is that they always work with a given efficiency, minimum downtime and response speed.
In accordance with this, the availability of information resources is ensured by:
- the use of a structural architecture, which means that individual modules can be disabled or quickly replaced if necessary without affecting other elements of the information system;
- ensuring fault tolerance due to: the use of autonomous elements of the supporting infrastructure, the introduction of excess capacity in the configuration of software and hardware, redundancy of hardware, replication of information resources within the system, Reserve copy data, etc.
- ensuring maintainability by reducing the time for diagnosing and eliminating failures and their consequences.
Another type of information security means is secure communication channels.
Functioning information systems is inevitably associated with the transfer of data, so it is also necessary for enterprises to ensure the protection of transmitted information resources using secure communication channels. The possibility of unauthorized access to data during the transmission of traffic through open communication channels is due to their general availability. Since "communications throughout their entire length cannot be physically protected, therefore it is better to initially proceed from the assumption of their vulnerability and provide protection accordingly" . For this, tunneling technologies are used, the essence of which is to encapsulate data, i.e. pack or wrap the transmitted data packets, including all service attributes, in their own envelopes. Accordingly, the tunnel is a secure connection through open communication channels, through which cryptographically protected data packets are transmitted. Tunneling is used to ensure traffic confidentiality by hiding service information and ensuring the confidentiality and integrity of transmitted data when used together with cryptographic elements of an information system. The combination of tunneling and encryption makes it possible to implement a virtual private network. At the same time, the endpoints of tunnels that implement virtual private networks are firewalls that serve the connection of organizations to external networks.

Firewalls as points of implementation of virtual private networks service
Thus, tunneling and encryption are additional transformations performed in the filtering process. network traffic along with address translation. Tunnel ends, in addition to corporate firewalls, can be personal and mobile computers employees, more precisely, their personal firewalls and firewalls. Thanks to this approach, the functioning of secure communication channels is ensured.
Information security procedures
Information security procedures are usually divided into administrative and organizational levels.
- Administrative procedures include general actions taken by the organization's management to regulate all work, actions, operations in the field of ensuring and maintaining information security, implemented by allocating the necessary resources and monitoring the effectiveness of the measures taken.
- The organizational level represents the procedures for ensuring information security, including personnel management, physical protection, maintaining the operability of the software and hardware infrastructure, promptly eliminating security breaches and planning recovery work.
On the other hand, the distinction between administrative and organizational procedures is meaningless, since the procedures of one level cannot exist separately from another level, thereby violating the relationship of protection. physical layer, personal and organizational protection in the concept of information security. In practice, while ensuring information security, organizations do not neglect administrative or organizational procedures, therefore it is more logical to consider them as an integrated approach, since both levels affect the physical, organizational and personal levels of information protection.
The basis of complex procedures for ensuring information security is the security policy.
Information security policy
Information security policy in an organization, it is a set of documented decisions made by the management of the organization and aimed at protecting information and its associated resources.
In organizational and managerial terms, the information security policy can be a single document or drawn up in the form of several independent documents or orders, but in any case it should cover the following aspects of protecting the organization's information system:
- protection of information system objects, information resources and direct operations with them;
- protection of all operations related to the processing of information in the system, including processing software;
- protection of communication channels, including wired, radio channels, infrared, hardware, etc.;
- protection of the hardware complex from side electromagnetic radiation;
- management of the security system, including maintenance, upgrades and administrative actions.
Each of the aspects should be described in detail and documented in the internal documents of the organization. Internal documents cover three levels of the protection process: upper, middle and lower.
Documentation top level information security policies reflect the organization's basic approach to protecting its own information and compliance with national and/or international standards. In practice, there is only one top-level document in an organization, entitled "Information Security Concept", "Information Security Regulation", etc. Formally, these documents are not of confidential value, their distribution is not limited, but they can be issued in an edition for internal use and open publication.
The middle-level documents are strictly confidential and relate to specific aspects of the information security of the organization: the means of information protection used, the security of databases, communications, cryptographic tools and other information and economic processes of the organization. Documentation is implemented in the form of internal technical and organizational standards.
Documents of the lower level are divided into two types: work regulations and operating instructions. The work regulations are strictly confidential and are intended only for persons who, on duty, carry out work on the administration of individual information security services. Operating instructions can be either confidential or public; they are intended for the organization's personnel and describe the procedure for working with individual elements of the organization's information system.
World experience shows that the information security policy is always documented only in large companies that have a developed information system that imposes increased requirements for information security, medium-sized enterprises most often have only a partially documented information security policy, and small organizations in the vast majority do not care at all about documenting the security policy. Regardless of whether the documentation format is holistic or distributed, the basic aspect is the security mode.
There are two different approaches that form the basis information security policy:
- "Everything that is not forbidden is allowed."
- "Everything that is not allowed is prohibited."
The fundamental defect of the first approach is that in practice it is impossible to foresee all dangerous cases and prohibit them. Without a doubt, only the second approach should be used.
Organizational level of information security
From the point of view of information security, organizational procedures for ensuring information security are presented as "regulation of production activities and relationships between performers on a legal basis that excludes or significantly hinders the misappropriation of confidential information and the manifestation of internal and external threats" .
Personnel management measures aimed at organizing work with personnel in order to ensure information security include the separation of duties and the minimization of privileges. The division of duties prescribes such a distribution of competencies and areas of responsibility, in which one person is not able to disrupt a process that is critical to the organization. This reduces the chance of errors and abuse. Privilege minimization dictates that users be given only the level of access that is appropriate for their job function. This reduces the damage from accidental or intentional incorrect actions.
Physical protection means the design and implementation of measures for the direct protection of buildings that house informational resources organizations, adjacent territories, infrastructure elements, computer science, data carriers and hardware communication channels. These include physical access control, fire protection, supporting infrastructure protection, eavesdropping protection, and mobile system protection.
Maintaining the health of the software and hardware infrastructure is to prevent stochastic errors that threaten to damage the hardware complex, disrupt programs and lose data. The main directions in this aspect are to provide user and software support, configuration management, backup, media management, documentation and preventive maintenance.
Rapid resolution of security breaches has three main objectives:
- Incident localization and damage reduction;
- Identification of the offender;
- Prevention of repeated violations.
Finally, recovery planning allows you to prepare for accidents, reduce damage from them and maintain at least a minimal amount of ability to function.
The use of software and hardware and secure communication channels should be implemented in the organization on the basis of an integrated approach to the development and approval of all administrative and organizational regulatory procedures for ensuring information security. Otherwise, the adoption of separate measures does not guarantee the protection of information, and often, on the contrary, provokes leaks of confidential information, loss of critical data, damage to the hardware infrastructure and disruption of the software components of the organization's information system.
Information security methods
Modern enterprises are characterized by a distributed information system that allows you to take into account the distributed offices and warehouses of the company, financial accounting and management control, information from the customer base, taking into account the selection of indicators, and so on. Thus, the array of data is very significant, and the vast majority of it is information that is of priority importance for the company in commercial and economic terms. In fact, ensuring the confidentiality of data that has commercial value is one of the main tasks of ensuring information security in the company.
Ensuring information security at the enterprise should be regulated by the following documents:
- Information security regulation. It includes the formulation of goals and objectives for ensuring information security, a list of internal regulations on information security tools and a regulation on the administration of a company's distributed information system. Access to the regulations is limited to the management of the organization and the head of the automation department.
- Regulations for the technical support of information protection. Documents are confidential, access is limited to employees of the automation department and higher management.
- Regulations for the administration of a distributed information protection system. Access to the regulations is limited to employees of the automation department responsible for administering the information system and senior management.
At the same time, these documents should not be limited, but the lower levels should also be worked out. Otherwise, if the enterprise does not have other documents related to information security, this will indicate an insufficient degree of administrative information security, since there are no lower-level documents, in particular, instructions for operating individual elements of the information system.
Mandatory organizational procedures include:
- the main measures to differentiate personnel by the level of access to information resources,
- physical protection of the company's offices from direct penetration and threats of destruction, loss or interception of data,
- maintaining the functionality of the hardware and software infrastructure is organized in the form of automated backup, remote verification of storage media, user and software support is provided upon request.
This should also include regulated measures to respond to and eliminate cases of information security violations.
In practice, it is often observed that enterprises are not sufficiently attentive to this issue. All actions in this direction are carried out exclusively in working order, which increases the time for eliminating cases of violations and does not guarantee the prevention of repeated violations of information security. In addition, the practice of planning actions to eliminate the consequences after accidents, information leaks, data loss and critical situations is completely absent. All this significantly worsens the information security of the enterprise.
At the level of software and hardware, a three-level information security system should be implemented.

Minimum criteria for ensuring information security:
1. Access control module:
- a closed entrance to the information system has been implemented, it is impossible to enter the system outside of verified workplaces;
- access with limited functionality from mobile personal computers was implemented for employees;
- authorization is carried out according to logins and passwords formed by administrators.
2. Encryption and integrity control module:
- an asymmetric encryption method for transmitted data is used;
- arrays of critical data are stored in databases in encrypted form, which does not allow access to them even if the company's information system is hacked;
- integrity control is provided by a simple digital signature of all information resources stored, processed or transmitted within the information system.
3. Shielding module:
- implemented a system of filters in firewalls, allowing you to control all information flows through communication channels;
- external connections to global information resources and public communication channels can only be made through a limited set of verified workstations that have a limited connection to the corporate information system;
- secure access from employees' workplaces to perform their official duties is implemented through a two-level system of proxy servers.
Finally, with the help of tunneling technologies, a virtual private network must be implemented in the enterprise in accordance with typical model building to provide secure communication channels between different departments of the company, partners and customers of the company.

Although communications are carried out directly over networks with a potentially low level of trust, tunneling technologies, through the use of cryptographic tools, make it possible to provide reliable protection all transmitted data.
conclusions
The main goal of all measures taken in the field of information security is to protect the interests of the enterprise, one way or another related to the information resources that it has. Although the interests of enterprises are not limited to a specific area, they all center around the availability, integrity and confidentiality of information.
The problem of ensuring information security is explained by two main reasons.
- The information resources accumulated by the enterprise are valuable.
- Critical dependence on information technologies causes their wide application.
Given the wide variety of existing threats to information security, such as the destruction of important information, unauthorized use of confidential data, interruptions in the operation of the enterprise due to violations of the information system, we can conclude that all this objectively leads to large material losses.
In ensuring information security, a significant role is played by software and hardware tools aimed at controlling computer entities, i.e. hardware, software elements, data, forming the last and highest priority frontier of information security. The transmission of data must also be secure in the context of maintaining its confidentiality, integrity and availability. Therefore, in modern conditions, tunneling technologies are used in combination with cryptographic means to provide secure communication channels.
Literature
- Galatenko V.A. Information security standards. - M.: Internet University of Information Technologies, 2006.
- Partyka T.L., Popov I.I. Information Security. – M.: Forum, 2012.
Information Security, as well as information protection, the task is complex, aimed at ensuring security, implemented by the introduction of a security system. The problem of information security is multifaceted and complex and covers a number of important tasks. Information security problems are constantly exacerbated by the processes of penetration into all spheres of society technical means processing and transmission of data and, above all, computing systems.
To date, three basic principles have been formulated that information security should ensure:
data integrity - protection against failures leading to the loss of information, as well as protection against unauthorized creation or destruction of data;
confidentiality of information;
When developing computer systems, failure or errors in the operation of which can lead to serious consequences, questions computer security become top priority. There are many known measures aimed at ensuring computer security, the main ones being technical, organizational and legal.
Ensuring the security of information is expensive, not only because of the cost of purchasing or installing security, but also because it is difficult to expertly determine the boundaries of reasonable security and ensure that the system is properly maintained in a healthy state.
Security tools should not be designed, purchased, or installed until an appropriate analysis has been made.
The site analyzes information security and its place in the national security system, identifies vital interests in information sphere and threats to them. Issues considered information war, information weapons, principles, main tasks and functions of ensuring information security, functions state system to ensure information security, domestic and foreign standards in the field of information security. Considerable attention is also paid to the legal issues of information security.
Also considered general issues information protection in automated systems data processing (ASOD), the subject and objects of information protection, the tasks of protecting information in ASOD. The types of intentional security threats and methods of information protection in ASOD are considered. Methods and means of authenticating users and delimiting their access to computer resources, controlling access to equipment, using simple and dynamically changing passwords, methods of modifying the scheme are considered. simple passwords, functional methods.
Basic principles of building an information security system.
When building an information security system for an object, one should be guided by the following principles:
The continuity of the process of improving and developing the information security system, which consists in substantiating and implementing the most rational methods, methods and ways of protecting information, continuous monitoring, identifying bottlenecks and weaknesses and potential channels for information leakage and unauthorized access.
Comprehensive use of the entire arsenal of available means of protection at all stages of production and information processing. At the same time, all the means, methods and measures used are combined into a single, integral mechanism - an information security system.
Monitoring the functioning, updating and supplementing protection mechanisms depending on changes in possible internal and external threats.
Proper training of users and compliance with all established privacy practices. Without this requirement, no information security system can provide the required level of protection.
The most important condition for ensuring security is legality, sufficiency, maintaining a balance of interests of the individual and the enterprise, mutual responsibility of personnel and management, and interaction with state law enforcement agencies.
10) Stages of building information security
Stages of construction.
1. Comprehensive analysis of the information system
enterprises at various levels. Risk analysis.
2. Development of organizational and administrative and
regulatory documents.
3. Training, professional development and
retraining of specialists.
4. Annual reassessment of the state of information
enterprise security
11) Firewall
Firewalls and antivirus packages.
A firewall (sometimes called a firewall) helps improve the security of your computer. It restricts the information that comes to your computer from other computers, giving you more control over the data on your computer and providing your computer with a line of defense against people or programs (including viruses and worms) that try to connect to your computer without authorization. You can think of a firewall as a border post that checks for information (often referred to as traffic) coming from the Internet or local network. During this check, the firewall rejects or allows information to the computer according to the settings you have configured.
What does the firewall protect against?
A firewall MAY:
1. Block computer viruses and worms from accessing your computer.
2. Prompt the user to choose to block or allow certain connection requests.
3. Keep records (security log) - at the request of the user - recording allowed and blocked attempts to connect to the computer.
What does the firewall not protect against?
He can not:
1. Detect or neutralize computer viruses and "worms" if they have already got on the computer.
3. Block spam or unsolicited mail so that it doesn't go to your inbox.
HARDWARE AND SOFTWARE FIREWALLS
Hardware firewalls- individual devices that are very fast, reliable, but very expensive, so they are usually used only to protect large computer networks. For home users, firewalls built into routers, switches, wireless points access, etc. Combined router-firewalls provide double protection against attacks.
Software firewall is a security program. In principle, it is similar to a hardware firewall, but more “friendly” to the user: it has more ready-made settings and often has wizards that help with configuration. With it, you can allow or deny other programs access to the Internet.
Antivirus program(antivirus)- any program for detecting computer viruses, as well as unwanted (considered malicious) programs in general and for restoring files infected (modified) by such programs, as well as for prevention - preventing infection (modification) of files or operating system malicious code.
12) Classification of computing systems
Depending on the territorial location of subscriber systems
Computer networks can be divided into three main classes:
global networks(WAN - Wide Area Network);
regional networks (MAN - Metropolitan Area Network);
Local networks (LAN - Local Area Network).
Basic LAN topologies
The topology of a LAN is a geometric diagram of the connections of network nodes.
Topologies of computer networks can be very different, but
only three are typical for local area networks:
Ring,
star-shaped.
Any computer network can be viewed as a collection
Knot- any device directly connected to
transmission medium of the network.
Ring topology provides for the connection of network nodes of a closed curve - a cable of the transmission medium. The output of one network node is connected to the input of another. Information is passed around the ring from node to node. Each intermediate node between transmitter and receiver relays the sent message. The receiving node recognizes and receives only messages addressed to it.
The ring topology is ideal for networks that occupy a relatively small space. It does not have a central node, which increases the reliability of the network. Information relaying allows using any types of cables as a transmission medium.
The consistent discipline of servicing the nodes of such a network reduces its performance, and the failure of one of the nodes violates the integrity of the ring and requires the adoption of special measures to preserve the information transmission path.
Bus topology- one of the simplest. It is associated with the use of a coaxial cable as a transmission medium. Data from the transmitting network node is distributed over the bus in both directions. Intermediate nodes do not translate incoming messages. Information arrives at all nodes, but only the one to which it is addressed receives the message. The service discipline is parallel.
This provides a high performance LAN with a bus topology. The network is easy to expand and configure, and adapt to different systems The bus topology network is resistant to possible malfunctions individual nodes.
Bus topology networks are the most common at present. It should be noted that they have a small length and do not allow the use Various types cables within the same network.
Star topology is based on the concept of a central node to which peripheral nodes are connected. Each peripheral node has its own separate communication line with the central node. All information is transmitted through the central node, which relays, switches and routes information flows in the network.
The star topology greatly simplifies the interaction of LAN nodes with each other, allows the use of simpler network adapters. At the same time, the performance of a LAN with a star topology is entirely dependent on the central node.
In real computer networks more developed topologies can be used, representing in some cases combinations of the considered ones.
The choice of a particular topology is determined by the scope of the LAN, the geographical location of its nodes and the dimension of the network as a whole.
Internet- a worldwide information computer network, which is an association of many regional computer networks and computers that exchange information with each other via public telecommunications channels (dedicated telephone analog and digital lines, optical communication channels and radio channels, including satellite communication lines).
Provider- network service provider - a person or organization that provides services for connecting to computer networks.
Host (from the English host - "the host who receives guests")- any device that provides services in the "client-server" format in server mode on any interfaces and is uniquely identified on these interfaces. In a more particular case, a host can be understood as any computer, server connected to a local or global network.
network protocol- a set of rules and actions (sequence of actions) that allows you to connect and exchange data between two or more devices included in the network.
IP address (IP address, short for Internet Protocol Address)- a unique network address of a node in a computer network built using the IP protocol. The Internet requires global address uniqueness; in the case of working in a local network, the uniqueness of the address within the network is required. In the IPv4 version of the protocol, an IP address is 4 bytes long.
Domain name - a symbolic name that helps to find the addresses of Internet servers.
13) Peer-to-Peer Tasks
Norbert Wiener, the creator of cybernetics, believed that information has unique characteristics and cannot be attributed to either energy or matter. The special status of information as a phenomenon has given rise to many definitions.
In the ISO/IEC 2382:2015 vocabulary " Information Technology”is given the following interpretation:
Information (in the field of information processing)- any data presented in electronic form, written on paper, expressed at a meeting or in any other medium used by a financial institution for decision-making, movement Money setting rates, granting loans, processing transactions, etc., including software components of the processing system.
To develop the concept of information security (IS), information is understood as information that is available for collection, storage, processing (editing, transformation), use and transfer different ways, including in computer networks and other information systems.
Such information is of high value and can become objects of infringement by third parties. The desire to protect information from threats underlies the creation of information security systems.
Legal basis
In December 2017, the Information Security Doctrine was adopted in Russia. In the document, information security is defined as the state of protection of national interests in the information sphere. Under national interest in this case, the totality of the interests of society, the individual and the state is understood, each group of interests is necessary for the stable functioning of society.
Doctrine is a conceptual document. Legal relations related to ensuring information security are regulated by federal laws "On State Secrets", "On Information", "On Protection of Personal Data" and others. On the basis of the fundamental normative acts, government decrees and departmental normative acts are developed on particular issues of information protection.
Definition of information security
Before developing an information security strategy, it is necessary to accept a basic definition of the concept itself, which will allow the use of a certain set of methods and methods of protection.
Industry practitioners propose to understand information security as a stable state of protection of information, its carriers and infrastructure, which ensures the integrity and stability of information-related processes against intentional or unintentional impacts of a natural and artificial nature. Impacts are classified as IS threats that can cause damage to the subjects of information relations.
Thus, information security will be understood as a set of legal, administrative, organizational and technical measures aimed at preventing real or perceived information security threats, as well as at eliminating the consequences of incidents. The continuity of the information protection process should guarantee the fight against threats at all stages of the information cycle: in the process of collecting, storing, processing, using and transmitting information.
Information security in this sense becomes one of the characteristics of system performance. At each point in time, the system must have a measurable level of security, and ensuring the security of the system must be a continuous process that is carried out at all time intervals during the life of the system.
The infographic uses data from our ownSearchInform.
In the theory of information security, IS subjects are understood as owners and users of information, and users not only on an ongoing basis (employees), but also users who access databases in isolated cases, for example, government agencies requesting information. In a number of cases, for example, in banking information security standards, the owners of information include shareholders - legal entities that own certain data.
The supporting infrastructure, from the point of view of the basics of information security, includes computers, networks, telecommunications equipment, premises, life support systems, and personnel. When analyzing security, it is necessary to study all elements of systems, paying special attention to personnel as the carrier of most internal threats.
To manage information security and assess damage, an acceptability characteristic is used, thus, damage is determined as acceptable or unacceptable. It is useful for each company to approve its own criteria for accepting damage in monetary terms or, for example, in the form of acceptable harm to reputation. In public institutions, other characteristics may be adopted, for example, the impact on the management process or a reflection of the degree of damage to the life and health of citizens. Criteria of materiality, importance and value of information may change during the life cycle of the information array, therefore, they must be reviewed in a timely manner.
information threat in narrow sense the objective possibility of influencing the object of protection is recognized, which can lead to leakage, theft, disclosure or dissemination of information. In a broader sense, information security threats will include targeted informational impacts, the purpose of which is to cause damage to the state, organization, or individual. Such threats include, for example, defamation, deliberate misrepresentation, incorrect advertising.
Three main questions of the information security concept for any organization
What to protect?
What types of threats prevail: external or internal?
How to protect, by what methods and means?
Information security system
Information security system for a company - legal entity includes three groups of basic concepts: integrity, availability and confidentiality. Underneath each are concepts with many characteristics.
Under integrity refers to the resistance of databases, other information arrays to accidental or intentional destruction, unauthorized changes. The concept of integrity can be seen as:
- static, expressed in the immutability, authenticity of information objects to those objects that were created according to a specific technical assignment and contain the amount of information necessary for users for their main activities, in the required configuration and sequence;
- dynamic, implying the correct execution of complex actions or transactions that do not harm the safety of information.
To control dynamic integrity, special technical tools are used that analyze the flow of information, for example, financial, and identify cases of theft, duplication, redirection, and reordering of messages. Integrity as the main characteristic is required when decisions are made on the basis of incoming or available information to take actions. Violation of the order of commands or the sequence of actions can cause great damage in the case of describing technological processes, program codes, and in other similar situations.
Availability is a property that allows authorized subjects to access or exchange data of interest to them. The key requirement of legitimation or authorization of subjects makes it possible to create different levels of access. The failure of the system to provide information becomes a problem for any organization or user groups. An example is the unavailability of public service websites in the event of a system failure, which deprives many users of the opportunity to receive necessary services or information.
Confidentiality means the property of information to be available to those users: subjects and processes for which access is initially allowed. Most companies and organizations perceive confidentiality as a key element of information security, but in practice it is difficult to fully implement it. Not all data on existing channels of information leakage is available to the authors of information security concepts, and many technical means of protection, including cryptographic ones, cannot be purchased freely, in some cases the turnover is limited.
Equal properties of information security have different values for users, hence the two extreme categories in the development of data protection concepts. For companies or organizations associated with state secrets, key parameter becomes privacy, for public services or educational institutions the most important parameter is accessibility.
Information Security Digest
Objects of protection in IS concepts
The difference in subjects generates differences in the objects of protection. Main groups of protected objects:
- information resources of all kinds (a resource is a material object: HDD, another medium, a document with data and details that help to identify it and attribute it to a certain group of subjects);
- the rights of citizens, organizations and the state to access information, the opportunity to obtain it within the framework of the law; access can be limited only by regulatory legal acts, the organization of any barriers that violate human rights is unacceptable;
- a system for creating, using and distributing data (systems and technologies, archives, libraries, regulations);
- a system for the formation of public consciousness (media, Internet resources, social institutions, educational institutions).
Each object involves a special system of measures to protect against threats to information security and public order. Ensuring information security in each case should be based on a systematic approach that takes into account the specifics of the object.
Categories and media
The Russian legal system, law enforcement practice and established social relations classify information according to accessibility criteria. This allows you to clarify the essential parameters necessary to ensure information security:
- information, access to which is restricted on the basis of legal requirements (state secret, commercial secret, personal data);
- information in open access;
- public information, which is provided under certain conditions: paid information or data for which access is required, for example, a library ticket;
- dangerous, harmful, false and other types of information, the circulation and dissemination of which is limited either by the requirements of laws or corporate standards.
Information from the first group has two protection modes. state secret, according to the law, this is information protected by the state, the free circulation of which can harm the security of the country. These are data in the field of military, foreign policy, intelligence, counterintelligence and economic activity states. The owner of this data group is directly the state. The bodies authorized to take measures to protect state secrets are the Ministry of Defense, the Federal Security Service (FSB), the Foreign Intelligence Service, Federal Service for technical and export control (FSTEC).
Confidential information- a more multifaceted object of regulation. The list of information that may constitute confidential information is contained in Presidential Decree No. 188 "On Approval of the List of Confidential Information". This is personal data; secrecy of the investigation and legal proceedings; official secret; professional secrecy (medical, notarial, lawyer); trade secret; information about inventions and utility models; information contained in personal affairs convicts, as well as information on the enforcement of judicial acts.
Personal data exists in open and confidential mode. The part of personal data that is open and accessible to all users includes the first name, last name, patronymic. According to Federal Law-152 "On Personal Data", personal data subjects have the right to:
- on informational self-determination;
- to access personal personal data and make changes to them;
- to block personal data and access to them;
- to appeal misconduct third parties committed in relation to personal data;
- for compensation for damages.
The right to is enshrined in the regulations on state bodies, federal laws, licenses for working with personal data issued by Roskomnadzor or FSTEC. Companies that professionally work with personal data of a wide range of people, for example, telecom operators, must enter the register maintained by Roskomnadzor.
A separate object in the theory and practice of information security is information carriers, access to which is open and closed. When developing the IS concept, protection methods are selected depending on the type of media. Main information carriers:
- printed and electronic means media, social media, other resources on the Internet;
- employees of the organization who have access to information based on their friendships, family, professional ties;
- means of communication that transmit or store information: telephones, automatic telephone exchanges, other telecommunications equipment;
- documents of all types: personal, official, state;
- software as an independent information object, especially if its version was finalized specifically for a particular company;
- electronic storage media that process data automatically.
For the purposes of developing information security concepts, information security tools are usually divided into regulatory (informal) and technical (formal).
Informal means of protection are documents, rules, events, formal ones are special technical means and software. The distinction helps to distribute areas of responsibility when creating information security systems: with general protection management, administrative personnel implement regulatory methods, and IT specialists, respectively, technical ones.
The basics of information security imply the division of powers not only in terms of the use of information, but also in terms of working with its protection. This separation of powers requires several levels of control.
Formal remedies
A wide range of technical means of information security protection includes:
Physical means of protection. These are mechanical, electrical, electronic mechanisms that operate independently of information systems and create barriers to access to them. Locks, including electronic ones, screens, blinds are designed to create obstacles for the contact of destabilizing factors with systems. The group is supplemented by means of security systems, for example, video cameras, video recorders, sensors that detect movement or exceeding the degree electromagnetic radiation in the area of location of technical means of removing information, embedded devices.
Hardware protection. These are electrical, electronic, optical, laser and other devices that are built into information and telecommunication systems. Before introducing hardware into information systems, compatibility must be verified.
Software - these are simple and systemic, complex programs designed to solve particular and complex tasks related to the provision of information security. An example of complex solutions are and: the first serve to prevent leakage, reformatting information and redirecting information flows, the second - provide protection against incidents in the field of information security. Software tools are demanding on the power of hardware devices, and additional reserves must be provided during installation.
can be tested for free for 30 days. Before installing the system, SearchInform engineers will conduct a technical audit at the customer's company.
TO specific means information security includes various cryptographic algorithms that allow you to encrypt information on the disk and redirected through external communication channels. The transformation of information can occur with the help of software and hardware methods that work in corporate information systems.
All means that guarantee the security of information should be used in conjunction, after a preliminary assessment of the value of information and comparing it with the cost of resources spent on protection. Therefore, proposals for the use of funds should be formulated already at the stage of systems development, and approval should be made at the level of management that is responsible for approving budgets.
In order to ensure safety, it is necessary to monitor all modern developments, software and hardware protection, threats and timely make changes to their own protection systems against unauthorized access. Only the adequacy and prompt response to threats will help achieve a high level of confidentiality in the company's work.
The first release was released in 2018. This unique program compiles psychological portraits of employees and distributes them by risk groups. This approach to ensuring information security allows you to anticipate possible incidents and take action in advance.
Informal remedies
Informal remedies are grouped into normative, administrative, and moral and ethical ones. At the first level of protection, there are regulatory tools that regulate information security as a process in the organization's activities.
- Regulatory means
In world practice, when developing regulatory tools, they are guided by information security standards, the main one is ISO / IEC 27000. The standard was created by two organizations:
- ISO - International Commission for Standardization, which develops and approves most of the internationally recognized methods for certification of the quality of production and management processes;
- IEC - the International Energy Commission, which introduced its understanding of information security systems, means and methods of its provision into the standard
The current version of ISO / IEC 27000-2016 offers ready-made standards and proven methodologies necessary for the implementation of information security. According to the authors of the methods, the basis of information security lies in the systematic and consistent implementation of all stages from development to post-control.
To obtain a certificate that confirms compliance with information security standards, it is necessary to implement all recommended practices in full. If there is no need to obtain a certificate, it is allowed to take any of the more early versions standard, starting with ISO / IEC 27000-2002, or Russian GOSTs, which are advisory in nature.
Based on the results of studying the standard, two documents are being developed that relate to information security. The main, but less formal, is the concept of enterprise information security, which determines the measures and methods for implementing an information security system for information systems of an organization. The second document that all employees of the company are required to comply with is the regulation on information security, approved at the level of the board of directors or the executive body.
In addition to the position at the company level, lists of information constituting a trade secret, annexes to employment contracts, fixing responsibility for the disclosure of confidential data, other standards and methods should be developed. Internal rules and regulations should contain implementation mechanisms and responsibilities. Most often, the measures are disciplinary in nature, and the violator must be prepared for the fact that the violation of the trade secret regime will be followed by significant sanctions, up to and including dismissal.
- Organizational and administrative measures
As part of the administrative activities to protect information security, there is room for creativity for security officers. These are architectural and planning solutions that allow you to protect meeting rooms and executive offices from eavesdropping, and the establishment of various levels of access to information. Important organizational measures will be certification of the company's activities according to ISO/IEC 27000 standards, certification of individual hardware and software systems, certification of subjects and objects for compliance with the necessary security requirements, and obtaining licenses necessary to work with protected information arrays.
From the point of view of regulating the activities of personnel, it will be important to design a system of requests for access to the Internet, external e-mail, other resources. A separate element will be the receipt of electronic digital signature to enhance the security of financial and other information that is transmitted to government agencies via e-mail channels.
- Moral and ethical measures
Moral and ethical measures determine a person's personal attitude to confidential information or information limited in circulation. Increasing the level of knowledge of employees regarding the impact of threats on the company's activities affects the degree of consciousness and responsibility of employees. To combat violations of the information regime, including, for example, the transmission of passwords, careless handling of media, the dissemination of confidential data in private conversations, it is necessary to emphasize the personal conscience of the employee. It will be useful to establish performance indicators for personnel, which will depend on the attitude towards corporate system IB.
