Open password-protected crypt files with Elcomsoft Forensic Disk Decryptor. Elcomsoft Forensic Disk Decryptor - full decryption of encrypted hard drives Memory visualization tool, kernel level
Read also
ElcomSoft software package for removing password protection with the maximum number of supported data formats, protection systems and encryption algorithms. The set includes all the company's password recovery products.
System requirements:
Windows: 7, 8, 8.1, 10, Server 2012, Server 2016, Server 2019
Torrent Password recovery software - ElcomSoft Password Recovery Bundle Forensic Edition 2019 in detail:
ElcomSoft Password Recovery Bundle 2019 contains:
ElcomSoft Advanced Archive Password Recovery 4.54.110
ElcomSoft Advanced EFS Data Recovery Pro 4.50.51.1795
ElcomSoft Advanced IM Password Recovery 4.90.1805
ElcomSoft Advanced Intuit Password Recovery 2.0
ElcomSoft Advanced Lotus Password Recovery 2.11
ElcomSoft Advanced Mailbox Password Recovery 1.11.476
ElcomSoft Advanced Office Password Breaker Enterprise Edition 3.05.802
ElcomSoft Advanced Office Password Recovery Pro 6.34.1889
ElcomSoft Advanced PDF Password Recovery Enterprise 5.08.145
ElcomSoft Advanced Sage Password Recovery 2.30.383
ElcomSoft Advanced SQL Password Recovery 1.13.1786
ElcomSoft Advanced VBA Password Recovery 1.63
ElcomSoft Advanced WordPerfect Office Password Recovery 1.35
ElcomSoft Cloud eXplorer ECX Forensic 2.11.28407 Full
ElcomSoft Dictionaries 1.0.1110
ElcomSoft Distributed Password Recovery 4.10.1236
ElcomSoft Explorer for WhatsApp Standard 2.60.30943
ElcomSoft Forensic Disk Decryptor Common 2.10.567
ElcomSoft Internet Password Breaker Standard Edition 3.10.4770
ElcomSoft iOS Forensic Toolkit 5.0
ElcomSoft Lightning Hash Cracker 0.60
ElcomSoft Password Digger Standard 1.04.147
ElcomSoft Phone Breaker 8.30
ElcomSoft Phone Breaker 9.05.31064 Forensic Edition Windows
ElcomSoft Phone Password Breaker Professional 3.00.106
ElcomSoft Phone Viewer Forensic 4.40.31234
ElcomSoft Proactive Password Auditor 2.07.61
ElcomSoft Proactive System Password Recovery 6.60.568
ElcomSoft System Recovery 5.60.389 BootISO
ElcomSoft Wireless Security Auditor Pro 7.12.538
Description of package applications:
ElcomSoft Advanced Archive Password Recovery - decryption of protected ZIP archives and RAR and recovery of original passwords. Maximum recovery performance complex passwords. Some types of archives are guaranteed to be decrypted within an hour.
ElcomSoft Advanced EFS Data Recovery Pro - decrypting files encrypted with NTFS using Encrypting File System(EFS).
ElcomSoft Advanced IM Password Recovery - Instantly extract passwords from dozens of instant messaging programs. Support for ICQ, AOL, MSN, Yahoo!, Mail.ru clients, Jabber, Picasa, QIP and many more. The extracted passwords can be used to compile a dictionary, with the help of which it is possible to significantly speed up the search for passwords for encrypted files.
ElcomSoft Advanced Intuit Password Recovery - restore access to password-protected Intuit Quicken and QuickBooks documents.
ElcomSoft Advanced Lotus Password Recovery - instant recovery of passwords of any complexity for Lotus SmartSuite documents.
ElcomSoft Advanced Mailbox Password Recovery - guaranteed password recovery for email clients and accounts Email POP3 and IMAP. Retrieve the username and password stored on the user's computer. Built-in POP3/IMAP server emulator to intercept POP3 and IMAP passwords from any mail clients, including mobile applications.
ElcomSoft Advanced Office Password Breaker Enterprise Edition - guaranteed recovery of access to encrypted documents in Microsoft applications Office 97/2000 in minutes.
ElcomSoft Advanced Office Password Recovery Pro - Guaranteed recovery of access to encrypted documents in application format Microsoft Office 97/2000 in minutes.
ElcomSoft Advanced PDF Password Recovery Enterprise - guaranteed removal of restrictions on editing, printing and copying PDF files. Password recovery to open a document with support for hardware acceleration. The patented Thunder Tables technology guarantees recovery of 40-bit keys within a minute.
ElcomSoft Advanced Sage Password Recovery - guaranteed access to protected ACT documents! Replacing and recovering passwords for BLB, MUD and ADF/PAD documents created with the ACT! Working remotely does not require ACT! on the computer.
ElcomSoft Advanced SQL Password Recovery - guaranteed recovery of access to password-protected databases Microsoft data SQL Server. Instant reset or change of any user or database administrator password in Microsoft format SQL Server.
ElcomSoft Advanced VBA Password Recovery is a tool for recovering, deleting and replacing passwords for Microsoft documents Office, OpenOffice, Apple iWork and Hangul Office with support for hardware acceleration with graphics cards.
ElcomSoft Advanced WordPerfect Office Password Recovery - instant password recovery for Corel WordPerfect Office documents. Extract passwords from WordPerfect, Quattro Pro and Paradox within seconds.
ElcomSoft Cloud eXplorer ECX Forensic - extract and view data from accounts google records. Passwords and browsing history are retrieved, user location data for the entire period of existence account, mail messages and contacts, Google Keep notes, bookmarks, history search queries, calendars and more. Password and no-password authentication is supported.
ElcomSoft Distributed Password Recovery is a powerful solution for corporate clients government organizations. Recovering passwords for dozens of file formats, documents, keys and certificates on clusters of computers united in a single distributed computer network.
ElcomSoft Explorer for WhatsApp Standard - a tool for extracting, viewing and analyzing communications WhatsApp users with iOS and Android support.
ElcomSoft Forensic Disk Decryptor Common - instant decryption or mounting of BitLocker, FileVault 2, PGP, TrueCrypt and VeraCrypt crypto containers using passwords, escrow keys and encryption keys extracted from an image random access memory, swap file, or hibernation.
ElcomSoft Internet Password Breaker - Instantly extract available passwords for websites, accounts and mailboxes from many applications. Support for saved fields and passwords in Internet Explorer, Edge, Chrome, Firefox, Opera, Outlook and Outlook Express, Windows Mail and Windows Live Mail.
ElcomSoft iOS Forensic Toolkit is a specialized tool for extracting data from devices running Apple iOS methods of physical and logical analysis.
ElcomSoft Password Digger Standard - decryption of the contents of system and user protected keychain storages macOS systems(OSX). Saving the list of passwords in text file, which can be used as a dictionary to speed up password brute force with appropriate tools.
ElcomSoft Phone Breaker - extract information from devices running iOS, Windows Phone, Windows 10 Mobile and BlackBerry 10, decrypt backups and guess unknown passwords using hardware acceleration.
ElcomSoft Phone Password Breaker - extract information from devices running iOS, Windows Phone, Windows 10 Mobile and BlackBerry 10, decrypt backups and guess unknown passwords using hardware acceleration.
ElcomSoft Phone Viewer Forensic is a simple, convenient and compact tool for viewing information retrieved from devices running iOS, BlackBerry and Mobile Windows. The product supports Elcomsoft Phone Breaker output formats and standard formats reserve copies of iTunes and Blackberry Link.
ElcomSoft Proactive Password Auditor - corporate security policy audit. The product will allow you to find out the degree of security local network by launching full scale attacks on account passwords. By detecting weak and insecure passwords, the product identifies weaknesses in the protection of the local network.
ElcomSoft Proactive System Password Recovery - recover many types of passwords and view hidden Windows information. extraction WiFi dongles(WEP and WPA-PSK), VPN, RAS, dial-up passwords, network resources, connections and RDP.
ElcomSoft System Recovery BootISO will help you restore access to accounts Windows, including local, network and account Microsoft records account. Resetting and restoring original passwords is supported.
ElcomSoft Wireless Security Auditor - security audit wireless networks Wi-Fi, checking the congestion of wireless networks and channels. Capturing packets using a dedicated or household wireless adapter Wi-Fi and full blown WPA/WPA2 password attack.
Treatment procedure:
Each program has instructions and medicine in a folder with installation files. This is usually a key or file replacement.
Released New Product for computer forensics called Forensic Disk Decryptor.
With the advent of this product, popular encryption tools hard drives, including technologies such as BitLocker, TrueCrypt and PGP, can no longer be considered reliable data protection: a program costing about $ 300 allows you to get almost any information from a protected drive without having the original access key.
Encryption of hard drives has already become a standard for many companies in the world, since it provides quite reliable protection secret data in case of theft or loss of equipment. Among the available technologies that allow encryption HDD In general, the most popular are just the three technologies targeted by Elcomsoft's Forensic Disk Decryptor utility - BitLocker, TrueCrypt, and PGP. If so far there have been only a few complaints about these technologies, now forensic experts will be able to extract information from encrypted media without having to obtain a key from the owner of these media.
So far, to open encrypted media, solutions like those from the same Elcomsoft company have been used. Usually, an attempt to open the disk was carried out by guessing the password using brute-force search. Unlike these traditional methods, the Forensic Disk Decryptor utility takes a slightly different approach: the program tries to detect traces of encryption keys in RAM dumps and hibernation files taken from the machine under investigation.
The only condition for a successful search for encryption keys is that the machine under investigation must be running, and the encrypted volumes must be mounted on the system. It does not matter if the desktop of the computer is locked or not. Moreover, the required disk encryption key can be retrieved even when the machine under investigation is hibernating.
As Vladimir Katalov, head of ElcomSoft, explains, the main and only drawback of crypto containers is the human factor. The fact is that in order to access protected data, it is necessary that the encrypted volume be mounted in file system. Few people like to enter a disk password every time a file is read or written, so in the vast majority of solutions the password is entered once per session and stored in RAM the rest of the time. It is logical to assume that if the encryption password needs to be constantly kept “at hand” (in RAM), then there is always a theoretical possibility of extracting this password using a third-party program.
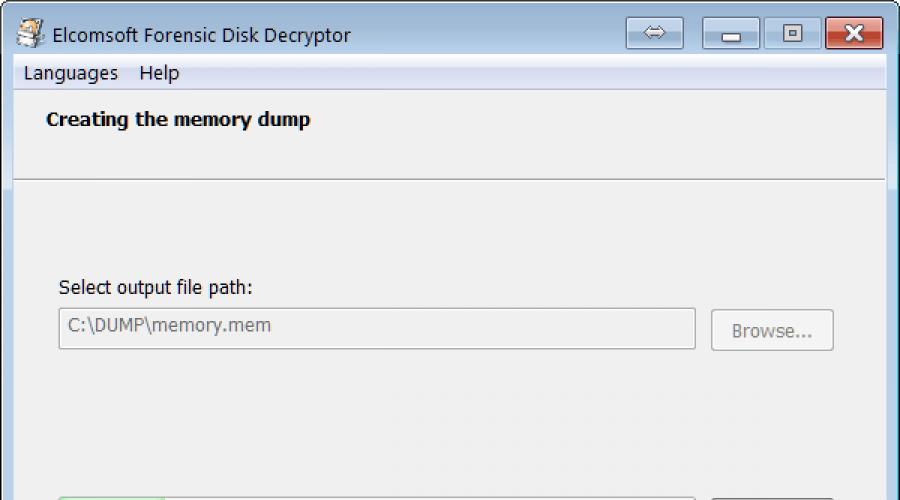
RAM Imaging Tool
Elcomsoft Forensic Disk Decryptor includes a tool that allows you to take an image of your computer's RAM. The tool works through a low-level driver that runs in the kernel mode of the system. 32- and 64-bit versions of the driver are supplied, compatible with operating systems Windows 7, 8, 10 and corresponding server editions. The driver is digitally signed by Microsoft and is fully compatible with the latest builds of Windows 10 Fall Creators Update That Check Out digital signature drivers.
It is recommended to run the RAM image removal utility from an external USB drive on which the portable version of Elcomsoft Forensic Disk Decryptor is deployed.
Portable installation
Elcomsoft Forensic Disk Decryptor users can deploy the portable version of the toolkit on an external USB drive. Portable version necessary for technical expertise and forensic analysis. It runs directly from the installation media, does not require installation or configuration on the user's computer and does not make modifications system registry or file system.
Decryption of BitLocker, FileVault 2, PGP, TrueCrypt and VeraCrypt crypto containers
Elcomsoft Forensic Disk Decryptor is designed to decrypt BitLocker, FileVault 2, PGP, TrueCrypt and VeraCrypt crypto containers and perform forensic examination of data stored in encrypted volumes. Both fixed and portable media are supported, including PGP in full-disk encryption mode, as well as removable drives protected with BitLocker To Go.
With Elcomsoft Forensic Disk Decryptor, you can either fully decrypt the contents of a protected volume, or work in real time with mounting encrypted volumes and decrypting selected data on the fly.
Product features
Elcomsoft Forensic Disk Decryptor provides access to information stored in encrypted volumes created by BitLocker, PGP and TrueCrypt crypto containers, allowing you to fully decrypt data or mount encrypted volumes for quick access in real time with file decryption on the fly.
Full decryption, mount or attack
Two modes of access to encrypted information are supported: full decryption and real-time access mode.
Full decryption of protected data
In this mode, Elcomsoft Forensic Disk Decryptor automatically decrypts all data stored in the crypto container. This mode gives the most full access with protected data, decrypting absolutely all files from the encrypted volume.
Connecting cryptocontainers and decrypting data "on the fly"
In real-time mode, access to data is provided instantly. The crypto container is mounted in the system as new disk, after which the data can be extracted using the standard Explorer - or any other tool for working with files. The information is decrypted on the fly, in the process of reading the data.
The speed of reading data in real-time access mode is limited only by the speed of the hard disk.
Brute force passwords
In cases where it is not possible to extract cryptographic key, nor the access recovery key, access to the data may require the recovery of the original password. allows you to attack the password that protects the encrypted container using a series of modern technologies, including dictionary attack, mask attack, mutation attack, and brute force attack. (Excluding VeraCrypt)
Extracting decryption keys
Elcomsoft Forensic Disk Decryptor extracts the keys with which the data was encrypted. With the help of these keys, decryption is carried out in real time - almost instantly.
The product supports several methods for extracting decryption keys.
- Hibernation file analysis (tested computer is turned off);
- Analyzing a snapshot of the computer's RAM (can be obtained using the built-in utility)
- Attack through the FireWire port (the computer must be turned on and the encrypted volumes must be connected). To carry out an attack through the FireWire port, you need additional computer with established free product(for example, Inception).
- Removing an image of RAM using the built-in tool (it is possible to run from a USB drive)
Use of passwords and escrow keys
Elcomsoft Forensic Disk Decryptor provides the ability to mount or fully decrypt crypto containers with a known password or a deposited key. Escrowed FileVault 2 keys can be retrieved from the cloud Apple service iCloud via Elcomsoft Phone Breaker and BitLocker keys can be obtained from Active Directory or from an account Microsoft user account.




Main advantages of the product
Access to data and work with cryptocontainers is provided without changing their contents. The authenticity and immutability of the information received is guaranteed.
The decryption key is required to gain access to the encrypted data and decrypt the contents of the crypto container. Elcomsoft Forensic Disk Decryptor supports three key extraction methods. The choice of one or another method depends on whether the computer under study is turned on or off, as well as on whether it is possible to run a program for taking an image (“cast”) of RAM on the computer under study.
Computer off: in this case, the keys are retrieved from the hibernation file. Protected volumes must be mounted before shutting down the computer. If the crypto container was unmounted before creating the hibernation file, it will not be possible to extract keys from it.
Computer turned on: if possible, a program for taking a snapshot of RAM is launched on the computer under study. The contents of RAM are saved to a file, from which Elcomsoft Forensic Disk Decryptor extracts the decryption keys. Encrypted volumes must be mounted when the snapshot is taken; otherwise, the decryption key cannot be retrieved. Detailed description this technology (and full list both commercial and free programs available at http://www.forensicswiki.org/wiki/Tools:Memory_Imaging).
The computer is turned on in restricted access mode: if it is impossible to launch programs on the computer under investigation (privileges are missing, there is no password for the user account, etc.), keys can be extracted by attacking through the FireWire port. The attack is carried out from a separate computer or laptop connected to the computer under investigation via the FireWire interface. Used to carry out an attack free utility, installed separately (for example, Inception: http://www.breaknenter.org/projects/inception/). This type attacks gives a result close to one hundred percent. Encrypted volumes must be mounted at the time of the attack.
After extracting the decryption keys, they are stored in the database, after which Elcomsoft Forensic Disk Decryptor will offer to fully decrypt the contents of the cryptocontainer or mount the protected volumes as new disks for on-the-fly decryption.
If it is not possible to extract the encryption keys and the recovery keys are not available, EFDD will extract from the encrypted volume the data necessary to launch a distributed attack using Elcomsoft Distributed Password Recovery.
Elcomsoft Forensic Disk Decryptor supports encrypted volumes, disks and portable media protected with BitLocker, FileVault 2, PGP and TrueCrypt, as well as RAW (DD) disk images. Supports encryption of flash cards using BitLocker To Go, as well as full disk encryption using PGP.
Product Video
This tool can extract data from an encrypted disk volume (FileVault 2, PGP, BitLocker, or TrueCrypt) using a binary encryption key stored in the computer's RAM.
- Key extraction by analyzing memory dump files or hibernation files will help the new release of Elcomsoft Forensic Disk Decryptor, including everything that was missing in more early versions. Plain text passwords and recovery keys, a Microsoft-signed kernel-level RAM visualization tool, is now available in the long-awaited portable version and support for the standard EnCase .E01 snapshot and encrypted DMG snapshots. Automatic detection all encrypted volumes and providing detailed information about the encryption method used for each volume. Let's run the program and see an example.
- Run Elcomsoft Forensic Disk Decryptor 2.0 and open an encrypted disk or disk image. EFDD scans the drive and identifies all encrypted volumes available on that drive. The volumes along with the corresponding encryption settings are displayed in the main window, picture below:
- IN previous versions were limited to mounting or decrypting volumes using binary cryptographic keys extracted from a computer memory image or hibernation file. The vulnerability in the use of cleartext passwords or escrow keys to access data stored in encrypted containers was very scarce.
- In EFDD 2.0. added new ways to mount or decrypt encrypted volumes. You can also use a binary cryptographic key, if you know the password of the original container, then it can be entered to mount the volume for its full decryption or offline analysis.
- Another way to access encrypted data is to use an escrow key or recovery key as they are sometimes called. Escrow keys offer backup sorting, allowing the rightful owner to decrypt the data if the password is lost, forgotten.
- For BitLocker encrypted volumes, the recovery key can be retrieved from Active Directory or from personal accounts, Microsoft user account at this link:
- For decrypting BitLocker volumes, check out the official Elcomsoft blog and. You can also find out what's changed in BitLocker in the November Update on the Microsoft website.
- For FileVault 2, you can extract the recovery key from Apple iCloud, then you will need a utility.
- EFDD was originally made to scan a computer's volatile memory. In the picture below, EFDD looks for cryptographic keys that are used to access data stored in encrypted containers. If the cryptographic key is found, then decrypting the container will not be difficult and there will be no need to attack the original plaintext password.
- Initially, Elcomsoft Forensic Disk Decryptor relied on memory images captured by third-party tools. Version 2.0 ships with an already available emergency memory imaging tool that uses level zero access to the computer's RAM. The RAM Processing Tool includes a kernel-mode driver that is digitally signed by Microsoft and is fully compatible with both 32-bit and 64-bit versions of Windows.
- Because you need access to all areas of the computer's memory, including areas that are actively protected using system or third-party anti-dumping and anti-debugging tools. Some utilities, programs, data collection run in user mode and they are denied access to certain protected, as I wrote above, areas in the computer's RAM. ElcomSoft comes with a kernel level driver that runs in the most privileged "zero" environment of the system, having full and unrestricted access to all areas of the computer's memory, that's cool!
- A Microsoft digitally signed driver allows a utility, a program, to be installed (or run) on the computer that verifies the driver's signature. Actually, to have everything without restrictions in all directions and areas, I will put it this way.
- The portable version also supports EnCase snapshots in the standard .EO1 format, as does the installation version, as well as encrypted DMG snapshots. The program can be run on running systems from a USB drive. To create a portable version, you need to install the utility on your computer and register it with your license key. Next, create a portable version of the utility, the picture below:
- Then you can use the newly created portable version of the program to capture the volatile memory of other computers, mount, decrypt encrypted volumes.
- If you have purchased the program before, then you can upgrade to it for free. latest version. If you want to purchase a license to use Elcomsoft Forensic Disk Decryptor 2.0, then go to the official website and get acquainted with the purchase offers. Good software always paid, this is a fact, of course there are exceptions, but they are very few. With this program, you get a good assistant who will restore your files in case of virus infection by ransomware. Just as I wrote above if you forgot or lost the password to the encrypted disk, container. If you have any questions, I will be happy to answer them in the comments below on this page.
What's new?
Overview of Elcomsoft Forensic Disk Decryptor 2.0
Decryption methods:
Memory visualization tool, kernel level. Find the key to open the crypto container.
Why does the image processing device, snapshot, require a kernel-level driver?
Creating a portable version of Elcomsoft Forensic Disk Decryptor 2.0
Elcomsoft Forensic Disk Decryptor is designed to decrypt BitLocker, FileVault 2, PGP, TrueCrypt and VeraCrypt crypto containers and perform forensic examination of data stored in encrypted volumes. Both fixed and portable media are supported, including PGP in full-disk encryption mode, as well as removable drives protected with BitLocker To Go.
With Elcomsoft Forensic Disk Decryptor, you can either fully decrypt the contents of a protected volume, or work in real time with mounting encrypted volumes and decrypting selected data on the fly.
Product features
- Decryption of information protected by the three most common crypto containers (BitLocker, FileVault 2, PGP, TrueCrypt and VeraCrypt)
- Support for portable media and memory cards protected by BitLocker To Go, as well as BitLocker volumes protected by a hardware TPM
- Support for the BitLocker XTS-AES format added in November windows update 10 (build 1511)
- Support for all PGP operating modes, including full-disk encryption mode
- Real-time access and full transcript
- Extraction of data decryption keys from hibernation files, computer RAM image file
- Embedded memory imaging tool running in system kernel mode and digitally signed by Microsoft
- Ability to create a portable installation to run from a USB drive
- Ability to decrypt volumes using text passwords and escrow keys
- Decrypting BitLocker volumes, including those protected by the TPM, using escrowed BitLocker Recovery Keys that can be retrieved from a Microsoft Account or Active Directory
- Decrypting PGP volumes with recovery key
- Decrypt FileVault 2 volumes with iCloud-escrowed keys (Elcomsoft Phone Breaker required to extract them)
- Extracts all keys from the RAM dump at once, even if there is more than one crypto container in the system
- Guarantee of the integrity and immutability of the studied data
- Support for both physical media and images in RAW (DD), EnCase .E01, DMG formats (including encrypted)
- Support for 32- and 64-bit Windows versions(starting from Windows XP and older, including Windows 10)
Elcomsoft Forensic Disk Decryptor exposes information stored in encrypted volumes created by BitLocker, PGP and TrueCrypt crypto containers, allowing you to fully decrypt data or mount encrypted volumes for fast real-time access with on-the-fly file decryption.
Full decryption, mount or attack
Two modes of access to encrypted information are supported: full decryption and real-time access mode.
Full decryption of protected data
In this mode, Elcomsoft Forensic Disk Decryptor automatically decrypts all data stored in the crypto container. This mode gives the most complete access to the protected data, decrypting absolutely all files from the encrypted volume.
Connecting cryptocontainers and decrypting data "on the fly"
In real-time mode, access to data is provided instantly. The crypto container is mounted in the system as a new disk, after which the data can be extracted using the standard Explorer or any other tool for working with files. The information is decrypted on the fly, in the process of reading the data.
The speed of reading data in real-time access mode is limited only by the speed of the hard disk.
Brute force passwords
In cases where neither the cryptographic key nor the recovery key can be retrieved, the original password may need to be recovered to access the data. allows you to attack the password that protects the encrypted container using a number of modern technologies, including dictionary attacks, mask attacks, using mutations and brute force. (Excluding VeraCrypt)
Data integrity and immutability guarantee
Access to data and work with cryptocontainers is provided without changing their contents. The authenticity and immutability of the information received is guaranteed.
Extracting decryption keys
Elcomsoft Forensic Disk Decryptor extracts the keys with which the data was encrypted. With the help of these keys, decryption is carried out in real time - almost instantly.
The product supports several methods for extracting decryption keys.
- Hibernation file analysis (tested computer is turned off);
- Analyzing a snapshot of the computer's RAM (can be obtained using the built-in utility)
- Attack through the FireWire port (the computer must be turned on and the encrypted volumes must be connected). An attack through the FireWire port requires an additional computer with a free product installed (for example, Inception).
- Removing an image of RAM using the built-in tool (it is possible to run from a USB drive)
Use of passwords and escrow keys
Elcomsoft Forensic Disk Decryptor provides the ability to mount or fully decrypt crypto containers with a known password or a deposited key. Escrowed FileVault 2 keys can be retrieved from the Apple iCloud cloud service using Elcomsoft Phone Breaker, and BitLocker keys can be retrieved from Active Directory or from a user's Microsoft Account.
Extracting keys to decrypt data
The decryption key is required to gain access to the encrypted data and decrypt the contents of the crypto container. Elcomsoft Forensic Disk Decryptor supports three key extraction methods. The choice of one or another method depends on whether the computer under study is turned on or off, as well as on whether it is possible to run a program for taking an image (“cast”) of RAM on the computer under study.
Computer off: in this case, the keys are retrieved from the hibernation file. Protected volumes must be mounted before shutting down the computer. If the crypto container was unmounted before creating the hibernation file, it will not be possible to extract keys from it.
Computer turned on: if possible, a program for taking a snapshot of RAM is launched on the computer under study. The contents of RAM are saved to a file, from which Elcomsoft Forensic Disk Decryptor extracts the decryption keys. Encrypted volumes must be mounted when the snapshot is taken; otherwise, the decryption key cannot be retrieved. A detailed description of this technology (and a complete list of both commercial and free programs is available at http://www.forensicswiki.org/wiki/Tools:Memory_Imaging).
The computer is turned on in restricted access mode: if it is impossible to launch programs on the computer under investigation (privileges are missing, there is no password for the user account, etc.), keys can be extracted by attacking through the FireWire port. The attack is carried out from a separate computer or laptop connected to the computer under investigation via the FireWire interface. To carry out the attack, a free utility is used, which is installed separately (for example, Inception: http://www.breaknenter.org/projects/inception/). This type of attack gives a result close to one hundred percent. Encrypted volumes must be mounted at the time of the attack.
After extracting the decryption keys, they are stored in the database, after which Elcomsoft Forensic Disk Decryptor will offer to fully decrypt the contents of the cryptocontainer or mount the protected volumes as new disks for on-the-fly decryption.
If it is not possible to extract the encryption keys and the recovery keys are not available, EFDD will extract from the encrypted volume the data necessary to launch a distributed attack using Elcomsoft Distributed Password Recovery.
RAM Imaging Tool
Elcomsoft Forensic Disk Decryptor includes a tool that allows you to take an image of your computer's RAM. The tool works through a low-level driver that runs in the kernel mode of the system. 32-bit and 64-bit versions of the driver are supplied, compatible with Windows 7, 8, 10 operating systems and corresponding server editions. The driver is digitally signed by Microsoft and is fully compatible with the latest builds of Windows 10 Fall Creators Update that verify the driver's digital signature.
It is recommended to run the RAM image removal utility from an external USB drive on which the portable version of Elcomsoft Forensic Disk Decryptor is deployed.
Portable installation
Elcomsoft Forensic Disk Decryptor users can deploy the portable version of the toolkit to external USB drive. The portable version is essential when conducting technical expertise and forensic analysis. It runs directly from the installation drive, does not require installation or configuration on the user's computer, and does not modify the system registry or file system.
Compatibility
Elcomsoft Forensic Disk Decryptor supports encrypted volumes, disks and portable media protected with BitLocker, FileVault 2, PGP and TrueCrypt, as well as RAW (DD) disk images. Supports encryption of flash cards using BitLocker To Go, as well as full disk encryption using PGP.