Multiple rdp sessions in xp. How to Enable Multiple Simultaneous Remote Desktop Connections or Sessions in Windows XP
Read also
To patch new versions (if the logic of the corresponding code section has not changed significantly), you must do the following:
0. The instruction is suitable for more or less educated, and most importantly, quick-witted specialists who can think. Those who are used to “copying” everything by Copy / Paste, I think, will not be able to cope and will breed “groans” and “lamentations” that “many letters”, “difficult” or “not strong” due to more fears and stereotypes of thinking than the complexity of the problem. This is their lot. Born to crawl, as you know, cannot fly. Don't let yourself dry out, Anon! Drink Iada or do the BUSINESS and start respecting yourself!
1. Download any - paid or free version Hiew
Even very ancient versions of the 90s are suitable, but if you need to patch x64, then you need 8.x (starting from the mid-2000s :)) Better, of course, to take a fresh one. The author has been developing the product for 25 years and there are few other such perfect creations of the programmer's skill.
2. Take termsrv.dll of some supported version - original and patched version. If there is no patched one, it is reasonable to assume that it needs to be patched with an existing patcher, don't be stupid! Start thinking! All required files put in a separate folder or folders. No need to try to edit anything on a single copy in system32. All the same, NOTHING WILL WORK (the entry is blocked in system32) and only sheep do this.
3. Compare patched and non-patched versions of the same dll using any binary file comparator. The Windows package includes the FC console utility. The command “FC /b termsrv.org termsrv.crk > differences.txt” leads to profit. The list of differences, and it is small there, 20 lines long, will go to the file differences.txt
Opening the file text editor and, either we leave it open, or we rewrite it on a piece of paper from which and to which offset the bytes changed. We immediately delve into and understand that all offsets and byte values, as below in Hiew, are indicated in the hexadecimal system, but this should not “scare” anyone, because you don’t even need to convert to decimal! (In case you need it, for general development- a screw calculator to help.)
In the list we see (identify) 3 conditional blocks, where the addresses are in a row. The first block is 2 bytes at the very beginning of the exe, at offsets 140-with-something-h (dll has the same format as exe, the only difference is that it contains only procedures and functions for external call - the so-called. exports, therefore, it will not be possible to directly execute it by renaming it to exe). This is the data, the offset search gets on the header of the exe file. These offsets store the checksum of the code-data (without a header), which Windows checks before starting, making sure that the file was not damaged and that something will not crash, respectively, when trying to execute it. We will return to them later.
This is followed by a change block of approximately 10 bytes. This is exactly what we will be studying. After it, there is another block of changes - the 6 most recent bytes of the executable. The bottom line is that instead of “zeroes”, the author has driven his sonorous name “deepxw” into the empty space at the end. A low bow to him for the patch and the idea, but there is no particular reason for us to repeat his “frills” when transferring the patch, therefore, those who wish can do it themselves, who have nothing to do on long winter evenings as part of the study “Drive ordinary letters into empty places in exe files using Hiew. However, this can be taken as a tribute to the author (it’s just that no one reads “there” there).
3. Open the original dll in one Hiew window, the patched one in another (run 2 copies of Hiew! In general, it is much more convenient to use Far - two things as a file manager and the basis for launching “these” Hiews). In both press F4 (Mode) and select Decode (F3). We will see a disassembled piece of the file from the very beginning. There is nothing to watch there, because Hiew is “trying” to disassemble the header of the EXE file, and this is data, not code. There is nothing to stare at, x-that he shows you, which is completely normal, because here you have to THINK, and not “copy”! Once again we are going and starting to think there is no need to try stupidly and literally follow the instructions ...
4. In both Hiews (in turn, damn it, we think ...) press F5 (Goto) and see that an input field has appeared at the top. There we drive in the address of the first difference (from the SECOND BLOCK!), found in the file of differences. FOR EXAMPLE, in Win7SP1x86Rus these are addresses around 19100h, and in VistaSP2Eng (x86 or x64 - xs), as I saw in the author's blog - addresses around 65200h. We get to the place of the first corrected byte.
The data in this Hiew window looks like this:
- In the first column - hex offset - from the beginning of the file, or in the process memory - depends on the Hiew mode selected by Alt-F1 (Global-Local). The default shows Local = as in memory if Hiew can figure out the code-data format. In our case, this does not present a problem, because the format of the exe file allows it to easily “figure everything out”. Therefore, one should not be afraid to see 06F2F8D51 there instead of the entered 19153. Memory addressing is important for understanding the addressing of the process, how it will look like when executed, appropriate for code analysis, if any.
– In the second column there is a hexadecimal code-data representation with parsing which code and which data refer to which instruction. Therefore, each line has a different length. It is shown so solely for your convenience. “Actually” (C) in the file itself, they are all “stuck” together in a row, which you can see in the “simple” view of hex data (F4-> Hex), where hex bytes are shown “stupidly” on the left through spaces, and on the right - "crazyabras" from the ASCII table that correspond to these bytes - as in "any" "good old" hex editor like WinHex, the screenshots of which you saw on "any" "coolhacker" website. We work with the same bytes all the time, as the computer itself does. The question is solely in their presentation and interpretation. When you copy an executable file from disk to disk, it's ALL DATA and NO CODE, because no one is executing anything. But it’s worth pointing out to Windows that this is an executable file, launching it, as Windows parses it into code and data and runs only the code from the place predetermined by the standard and the header, after which the code itself, executed by the processor, is parsed further in its structure and itself is divided again to code and data, and so on.
In the F4-> Decode mode, instead of “krakozyabr”, it shows us bytes and “true meaning”.
- In the third (right) and largest column (more precisely, a couple of columns), we are shown a disassembled code section - text, the so-called. “mnemonic” representation of this very code (assembly language), intended for somewhat simplified and understandable perception for a “reasonable person”, with his wonderful analog associative thinking, who perceives abstract “bare” code sequences with extreme difficulty.
5. Having made the transition to the desired offset in the previous paragraph, we see that the cursor (such a gray one :)) points to the beginning of a 6-byte command (in x64 there may be more bytes) to the right of which the cmp eax TYPE instruction is “disassembled”,
if you take one line above and a little below, then the TYPE construct will come out:
mov eax,
cmp eax,
jz .06F30B25E
push edi
push 020
call .06F2E1440
pop ecx
You don't need to be an "assembler expert" to understand this construct, although it is recommended that you have at least a basic knowledge of "programming in any language". But knowledge of the English language does not hurt!
The first instruction (which is not patched in any way, it is “above the first difference”) is called mov - which, excuse me, is the first association that comes to mind from in English? - correct - move - i.e. move. The instructions' arguments go in the second "subcolumn". eax and edi are the so-called. 32-bit registers are single memory cells in the process itself, designed to store data while it is being processed. Almost all registers are of the same type, theoretically anything can be written there, as long as it fits, but some of them are traditionally used to store certain types of data (so as not to get confused), for example, EAX, EBX, ECX, EDX are used directly for “user data”, moreover, ECX traditionally goes as a counter (for example, cycles), and ESI, EDI - as pointers to some current position in memory, addresses with which to work. And some of the registers are hardware-dependent and “it’s better not to touch them” - for example, the IP register automatically contains the address of the current instruction that the processor is executing, and if you try to write some of your data there - a variable of your program, then the percent will stupidly go to the instruction with this address and everything will crash. ESP - points to the stack - a kind of “bottle” into which the first one climbed will be the last to get out (Fist In Last Out), designed for temporary storage of data that does not fit in registers, but it makes no sense to drive them back into memory, after they will be used soon. To work with data, usually a byte - 8bits, a word - 16bits, a longword - 32bits, or a double longword 64bits (for 64-bit processors) is placed from memory into a register. To work with short data, you can access parts of the register (for example, eax consists of ax - the lower 16 bits and ah and al - parts of ax itself), but this is beyond our problem. Then some transformations are performed with the data in the register, after which the result is placed back into memory - into the same or another cell or any other allocated by the author (or his compiler) of the program for the corresponding purposes.
Addresses are in square brackets. If you need to take DATA from a memory cell at some address, and not the address itself, then simply write the address in square brackets. The TYPE construct means that the data must be taken from a memory cell that has an address whose value is obtained by adding the value in the ESI + 324h register. In Assembler, it is customary to write more clearly, but it was more convenient for the author of Hiew to show it this way, perhaps for clarity. When entering commands, Hiew accepts standard constructs like , as shown below.
In total, we understand that this instruction takes data (4 bytes = 32 bits) at the address and puts them in the EAX register. The next instruction ((which is already being patched) is CMP. The first thing that comes to mind for a fair-faced student who studied English diligently at school is compare. It's about about comparison. Otherwise, everything is the same as in the previous instructions. The address is just next door. Instruction
cmp eax,
compares the contents of the eax register and the memory location at . The previous instruction pushed a number from the adjacent cell into the eax register. Now it is compared with the number from the cell. What's so hard, sorry? Sheep can be taught! This is certainly easier than “multi-kilometer” objects from some kind of shit toad, pulling thousands of properties with them, in which you can drown ...
But what about the result? Compare compared, so what's the point, the attentive reader will ask ... How to find out where the dog rummaged? And the result is stored in a special flags register Flags. In this reserved register, each bit represents a flag. In particular, there is a zero flag - Zero. If, as a result of executing the comparison instruction, it turns out that the numbers are equal, the flag will be set (1), if not, then it will be reset (0) (or vice versa, too lazy to look at the debugger - it doesn’t matter here). Similarly, there is another checkbox for more or less - Sign. The flags change as a result of the execution of instructions that change them, and will remain in their position until they are changed as a result of another instruction that affects their state. Therefore, after cmp, we can execute any other instructions that depend on the state of the flag until we execute the one that changes it. The state of the flags is read by the conditional branch instructions and some others, and the result is some action or inaction of these instructions.
The next instruction is
jz .06F30B25E
Instructions that begin with J [almost] all mean Jump - jump, i.e. moving to another place. This instruction refers to conditional jump instructions and stands for Jump if Zero - i.e. jump to the address if the Zero checkbox is checked. If the checkbox is NOT checked, then “nothing will happen”. The transition address is given as an argument (they can be different, relative or absolute, “far” or “close” in memory. Here the address is indicated in the address space of the program, as it is configured by the exe header, there is no point in delving into it, it will only complicate everything. If If the previous instruction detected equality of the arguments, then the transition will occur, if not, then it will not occur and the processor will proceed to the next instruction.
Next 2 instructions
push edi
push 020
We recall that in English push means to shove, push. Here it means pushing the numbers onto the stack for temporary storage. Often, variables are saved this way before entering procedures, registers inside the procedure can be used for other purposes, and using the stack, you can both save register values and pass arguments to the procedure, which will pull them out after entering it, and shove the results there before exiting if available and required. The convenience is that you do not need to worry about allocating address space for storing temporary data of a significant amount. If you need to pass an array, just pass its address in memory. There is no reason to transfer all elements of the array, it will only uselessly gobble up memory and processor time, as is done with bydlocking. (When saving is required original copy array according to the logic of work - this is a different situation and the programmer himself consciously initiates the copying of the array for the purpose of replication.)
When working with the stack, the processor itself will take care of everything - the area for storing the stack is allocated by the operating system with the hardware support of the processor.
The first instruction will store the value of the EDI register - a pointer to a certain memory area, and the second will push the predefined constant 20h there. Probably some argument of the procedure, but it doesn’t matter to us because there is no need to do the analysis that the author of the patch did - we transfer the finished patch to another version of the program, and this is usually SIMPLE!
Next instruction
call .06F2E1440
In English, call means to call, to call.
It's about calling a procedure. There are no names in the procedure call code - there are addresses where their code is located. For convenience, disassemblers (including Hiew) can pull out the names of procedures and functions from the tables of imports and exports of exe files (there is supposed to be interaction different programs and “libraries” after compilation and procedures are given names by which they can be called from another program, but internal procedures are not named after compilation). Of course, there were names in the source codes, but after compilation they are useless ... They would only take up space. The processor does not need to know someone's names, it counts numbers ... Sometimes decompilers / disassemblers manage to pull out the names of procedures from debugging information (if the next bydlocoder forgot to chop it off and inflated the size of the binary with useless info) and this helps in code analysis, but in our case even this is poof. We do not need to understand why this procedure is needed and what it does ... I remind you that we have a ready-made patch, and if we manage to transfer it “without incident”, then there is no need to delve into it.
The last instruction given
pop ecx
Pop - the opposite action of push - i.e. pop the last value pushed onto the stack. In this case, the ecx register. Probably, this instruction is needed to extract the result of the procedure, but we don’t care, incl. and because this instruction, as well as 2 pushes above, and call, do not change after the patch and are given for some general presentation and as a landmark-border of the patch. After the patch, all these instructions will remain in place, like everything after them.
6. Now we take the patched termsrv.dll in another Hiew window, look at the same address for instructions.
mov eax,
mov eax, 000000100
nop
mov ,eax
push edi
push 020
call .06F2E1440
pop ecx
We see differences only in the second, third and fourth instructions.
Second mov eax, 000000100
just write the constant 100h (=256) into the eax register
Third nop
the most “funny” = NoOperation – does nothing at all and forever and ever. Why is she needed? And it is needed to align the synchronization according to the code-data. The fact is that the sizes of the original and patched code must completely match in the number of bytes and the boundaries of the commands (together with their arguments). If something shifts at least one byte, the processor will get “in the wrong place”, it will perceive a certain instruction argument as a command, and the bytes following it as arguments of this command, even if there is a different command code. Everything will move out immediately and fatally. 99% that the program will crash with a fatal error. The nop command has code 90h and occupies one byte. If there is redundant code that is not needed or even harmful for the purposes of the patch, it can be replaced, along with arguments, with as many nops in a row as it takes up bytes. Among hackers, this is called zanopat or zanopat. In fact, this the only way remove redundant code executable code, because this is not a text and any “cutting out from the middle” “for the purpose of shortening” will immediately lead to the fact that all addresses will shift, move out and nothing will work at all. And the “worst” thing happens when new code, which need to replace the old one, does not fit into the “old” place in any way ... This is where the hacker’s headache begins - how to squeeze it in order to fit in ...
Fourth mov ,eax
put the number from the eax register into a memory location
In principle, the third and fourth or third and second instructions can be swapped - this will not change anything. But nop cannot be removed in any way, because new commands are 1 byte less than the old ones in code length, and such a discrepancy, if it is not parried with nop, will immediately lead to a synchronization failure.
Comparison “with what was” immediately puts everything in its place!
It was - take the number from the cell, compare it with the number from the cell. If they are equal, then “somewhere” to jump, if not, then go further and perform the procedure. In the context of the task, this comparison of the number of allowed connections with the limit of allowed connections (i.e. 1 for workstation or 2 for the server). The limit is stored in some constant whose address is specified in the comparison instruction.
What happened is to take the number from the cell, forget about “this thing” and immediately overwrite the value of the EAX register with the constant 100h (= 256 - i.e., apparently, the new limit is 256 connections), and then put this number in the cell
Nobody compares anything, the procedure that is called below will always be executed. In addition, in the cell where, obviously, the connection limit was stored, a new limit = 256 is “forced” written in case there are other checks for this limit somewhere else in the program. THAT'S ALL! It is difficult to come up with something more primitive!
If we had to look for this place ourselves, then we would have to trace the procedures of this dll with a debugger, as the patch author obviously did, or disassemble everything with something like IDA and carefully study the code containing hundreds of thousands of instructions. But we're all set! It's like in a joke about a mechanic who once hit with a hammer and the car started up, but the subtlety is that he knew where to hit and it costs a lot of work. (Just don’t talk about money here - stick it in your ass! Especially on the eve of a great holiday! For fans of “making money on the Internet” - there are specialized sites.)
Why does the patch not work on all subsequent versions - because the addresses change and the code (its arguments) changes slightly during compilation. This leads to the shift of the desired code inside the exe to other offsets, and if you search by signature (strict byte sequence), it may not find the search arguments have changed. After all, many addresses are also arguments to instructions and change the binary code beyond recognition, despite the fact that its essence is still the same ... Do it manually! You have a head on your shoulders, and not a “strict sequence of convolutions” ...
7. Now in the ORIGINAL of the version of termsrv.dll that the patcher patches, you need to find some unique, in the context of the program, sequence of bytes NEAR the place that you need to patch in order to search for it in new version termsrv.dll, the one you want to patch, but the patcher won't patch it...
You need to look at the disassembler, and look for the BYTES corresponding to it, and if you choose something too “simple”, then such a combination will occur many times during the search and it will be difficult to find the right place, it will “sink” among a bunch of other similar ones. And for us, “hit accuracy” is extremely important, because if you patch “not there”, then it will not work, or even Windows will hang ...
You cannot select instructions containing long fixed addresses for the search string. When compiling other versions, they are likely to move out and you will not find anything on them in the new version.
The whole procedure where the check takes place is small, just a couple of dozen commands. For assembler, this is “nothing”. Hiew will show you the conditional boundaries of the procedure as "bands" _^_^_^_^_^_. Please note that at the beginning of the procedure, there is a call to the address of the "import" Windows API procedure - CDefPolicy:: Query and Hiew detected this (therefore, the function name was fished out and written). This should be a good guide for you on the way to the right place. In addition, this “however hints” that there may be another way to solve the problem, for example, finding some “secret” Policy responsible for the behavior of the Terminal Server. Those who wish can trace the code with a debugger and look for how a variable or constant is initialized with the number of connections. But “code from CDefPolicy” is not suitable for the search string, because the address of the procedure in the import will most likely move out in the new version. I would try searching by bytes from the beginning of the procedure after the CDefPolicy. There goes:
57 push edi
6A10 push 010
8BF1 mov esi,ecx
33DB xor ebx,ebx
out 57 6A 10 8B F1 33 DB
At the end, you can add another E8 call instruction code, following it, but NOT its argument (next bytes), because this is the address and it will change when new versions are compiled.
This sequence gives me when searching in Hiew (F7-Search)
Only 3 coincidences. Moreover, the call to CDefPolicy is visible in the context of only one case - in the first one. If you have the same - a place is found, write down its address from the first column (after pressing Alt-F1 - Global!) “on a piece of paper” and try to patch.
If the code has changed so much that it does not find anything, we are looking for other unique sequences, incl. gleaned in neighboring procedures and try to look for them. The task is to find the right code, where “everything matches in meaning”, and not a sequence, we think about this and look at the context, trying to find CDefPolicy::Query in the new version. You can search for the text CDefPolicy::Query in new.dll, you will find the string (multiple times), but not the place where its address is referenced. This method sometimes helps to find the right one using F6 (Reference) in Hiew and I managed to find the right place in the dll from Win7SP1x86Rus for the sake of experiment, but not the fact that it will work everywhere, especially with other programs).
8. Now you need to take the termsrv.dll of the version that you need to patch. We launch the third copy of Hiew, open a new dll in it” (in order to easily switch between all three and compare visually). We find the right place, as described just above, or go to the address that was written “on a piece of paper” (a piece of paper in general is a programmer’s friend in this mortal world where hard disks, knocks out traffic jams and hang OS).
We analyze the code below CDefPolicy::Query and easily find the right place, SIMILAR to:
cmp eax,
jz .06F30B25E
WE UNDERSTAND that the address is , but if it has changed, for example, this is the address we need and we will operate on it in further editing.
9. If you are convinced that you have exactly found what you need, hover over the cmp instruction and feel free to press F3-Edit. The “gray” cursor will change to “normal” (for the text display mode) - subscript. It must point to the same cmp instruction.
Press Tab (or F2) and the assembler instruction input dialog will appear.
Enter instructions there.
mov eax, 100
Then Enter. On the main screen, you will see that the bytes “from the instruction” have changed and some of them have become “gold” (yellow). At the same time, the instructions BELOW “moved out” and in the right column opposite them shows “rubbish” - not at all what was there before.
The command input dialog on top of the main window continues to “hang” and wait for the input of new instructions, while showing some next instruction, incorrectly interpreted due to the addressing congress.
We do not pay the slightest attention to this instruction and drive in the next one.
Type nop and press Enter
In the main window, the next line with code 90 will turn yellow.
Synchronization will be restored and the next command will again be jz. It will be offered to change the dialog for entering instructions.
drive in there
mov ,eax
If instead of 320 there was a different address in the cmp command, then drive it in!
Press Enter. after that, the code in line 3 will turn yellow, to the right of which there should be a mov, eax instruction (or not 320, but the number that was entered).
We check that the code-data synchronization has NOT moved out. The next instruction should be push edi (or another if the code has changed a lot and you had a different instruction there before the patch - it should remain in its place and be correctly interpreted, which means that everything is OK after it).
When everyone has driven in, press ONCE Esc. The instruction entry dialog will disappear, but it can be called up again at any time (in edit mode) by pressing Tab. All changed bytes will be yellow. Meticulously check that everything looks correct, they didn’t screw up anywhere. No one will check anything for you here, there are NO “protections from fools” of any rank and title. No one will take into account the regalia. What they did is what they got. Nakosyachili - freezes and will not work.
If everything is OK press F9 (Update). The changes will be written to a file on disk and the changed bytes will change color to normal (Cyan).
10. Now you need to correct the checksum of the exe. Doing this is insanely boring, I bet Hiew will do the job for you and you don't have to do much. Press F8 (Header). A “gray inconspicuous” window appears with a “decryption” of the parameters of the header of the exe file.
Press F3 (Edit). A “colored” purple appears over the “nondescript” window. It lists all header parameters with their addresses and values. With a boring face, we scroll towards the end and find the Checksum parameter there. On the right is its value (the checksum itself) in hexadecimal and decimal expression, which remained “inherited” from the original UNpatched file. Press F3 again and, lo and behold, the line turns yellow and the checksum changes its value. We can believe Hiew, or we can find it on forums or in books and calculate it manually. If everything suits you, press F9 (Update). Windows flicker, everything disappears ... This is the end, the uninitiated reader thinks. But when the dust settles, the checksum is correct. The distrustful can go back to the mentioned dialogue and compare the Checksum with the one carefully saved before the execution in the backup on a piece of paper. You can exit Hiew by Esc and proceed to the stage of testing your division.
11. Having received the patched file, you can try to replace termsrv.dll in the target OS.
Due to the protection mechanisms of Windows against changing system files, as well as the prohibition on recording running programs (sharing violation), it will be necessary to stop the Terminal services service (see the comments of other users above) and replace copies of the dll in “all sorts of WinSxS”, etc., so that unauthorized Windows even and forgot to think about trying to restore the unpatched version.
If everything works, then you have become a coolhacker or have taken the first CONSCIOUS step along the way. Nobody prevents you from picking and learning further, making the world a better and kinder place. The net has a lot of instructions and entire thematic forums for those who want to think with their own heads, and not just consume mass-produced porn from the Matrix.
Do not hesitate to publish a list of changed bytes (you can get it using the same “stock” “FC /b File1 File2″) for other, less sophisticated users, here and / or on other resources, do good to your neighbor, as the Lord bequeathed and glorify his name in the annals of hacker history.
According to the list of changes, you can make a .CRK file (for patchers who understand this ancient format), or make patch.exe using any patch maker, of which, over the years of evolution, tens and hundreds have written. Just choose then Windows support Vista/7″ because the old ones, though good-fit, don't know anything about Escalate privileges, and Windows will stupidly not allow them to patch anything in Windows/System or Program Files. The instructions should mention the requirement to stop the terminal service, or the use of patches on files in separate folders followed by substitution in system32 by the users themselves. In any case, publish the list of changes, do not complain about “laurels”, since someone may have to fuck manually and infa will allow you to find an alternative solution. The author's patcher does all this automatically, including working with WinSxS - I looked at the code, but I think it will not be easy to find a patchmaker that takes all this into account.
Windows XP Professional and Windows XP Media Center Edition (MCE) have connection service Remote Desktop (RDP), which allows you to remotely connect a computer, gain access and control from another computer or host. However, machines on the operating system Windows XP allow simultaneous remote desktop connection only one user who was connected to it, without multiple sessions remote desktop connections or support links.
Whenever a remote user connects through a client to Remote Desktop (RDC) to connect to host Windows XP, the local user is logged out with or without console lockout. Remote Desktop, as opposed to a terminal server service in Windows Server 2003 and Server 2008, is intended for single use by a user, whether the user is local or remote.
Here hack to unlock one limitation which allows multiple simultaneous Remote Desktop Connection sessions in Windows XP Professional and Media Center Edition using either the patched termserv.dll or the old patched termserv.dll build version 5.1.2600.2055, so that an unlimited number of users can simultaneously connect to computer using remote desktop.
- Download a patched copy that will remove the remote desktop connection restrictions disabled for your version of Windows XP:
Windows XP SP3: termsrv.dll (version 5.1.2600.5512)
For termsrv.dll information, the patch usually has the following bits of HEX codes, which are rewritten to the following values:
00022A17: 74 75
00022A69: 7F 90
00022A6A: 16 90
- Restart your computer and boot the information in safe mode by clicking F8 during bootstrap and select safe mode . This step is only necessary if you are currently using Windows Terminal Services or remote desktop services, protection file system must be skipped or the following error message will appear to restore the original termsrv.dll.
3.Go to %WINDIR%System32 and do backup(or rename) termsrv.dll .
4.Rename or delete termserver.dll in folder %WINDIR%System32 Dllcache.
5.Copy the downloaded termsrv.dll V %WINDIR%System32 , %WINDIR%ServicePackFiles i386(if any) and %WINDIR%System32 Dllcache .
6.Then download and run to merge the registry values into registery, or you can run the registry editor manually and add the following registry settings:
"EnableConcurrentSessions" = DWORD: 00000001
"AllowMultipleTSSessions" = DWORD: 00000001
7.Press the button Start -> Run and enter the command gpedit.msc, click Enter to open the Group Policy Editor.
8.Go to Computer Configuration -> Administrative Templates -> Windows Components -> Terminal Services .
9.Enable limit the number of connections and set the number of connections to 3 (or more). The setting allows more than one use of the computer at the same time.
10.Ensure that Remote Desktop is enabled on the Remote tab of System Properties by selecting the radio button Allow users to remotely connect to this computer .
11.Turn on fast user switching V Control panels -> user accounts -> Change User Login or Shutdown .
12.Reboot your computer normally.
I note, if you cannot replace or overwrite the termserv.dll file - access denied or file error, turn off "Termine Services" in the "Services" section of the Control Panel "Administrative Tools". In addition, each connected physical connection must have its own user account on the target computer, and must be authenticated with the corresponding own username and credential password.
To remove and return to the original termsrv.dll, simply remove the patched version and also rename the backup copy back to "termsrv.dll". If Terminal Services is enabled and running, you need to do it in safe mode.
If a computer with Windows XP connected to a domain local network, Windows will set the RegKey "AllowMultipleTSSessions" to "0" each time the computer is not restarted. In order for multiple or unlimited remote desktop sessions to be allowed in an AD domain environment, the data value for "AllowMultipleTSSessions" must be set to "1" each time the system starts. To change the value, just restart ts_multiple_sessions.bat every time you start your computer. Also, put ts_multiple_sessions.bat V C: Documents and Settings All Users Main Menu Programs Startup folder so that it will automatically run on the first user with administrator rights. Another solution is to install an additional service or define a key in the registry branch HKEY_LOCAL_MACHINE SOFTWARE Microsoft Windows CurrentVersion Run, through which the batch file works automatically on boot, and this is useful if the computer will not be logged on by anyone, but is still required by the worker to allow unlimited remote desktop connections to work.
Another thing is if the user closes remote connection Instead of ending the session, when he or she tries to log in again, an error code 4226 message will appear related to the TCP/IP event. To resolve this issue, download and install Windows XP TCP/IP Limiting Connection and Event ID 4226 patch, and set the connection to at least 50.
This assembly is built on the original image of Microsoft Windows XP Professional SP3 Russian version, with all the updates! The disk is multiboot. DOWNLOAD FOR FREE -
Greetings, dear readers, and Denis Trishkin is in touch again.
I recently came across a question like "Remote Desktop" (RDP Windows 7). This tool allows you to work with your computer using another device. So, for example, the user can use home equipment to perform all the necessary functions on a PC located in the office. Agree, in some situations this opportunity is convenient. But at the same time, you first need to debug everything correctly.
In order to enable rdp, you need to perform a few steps:
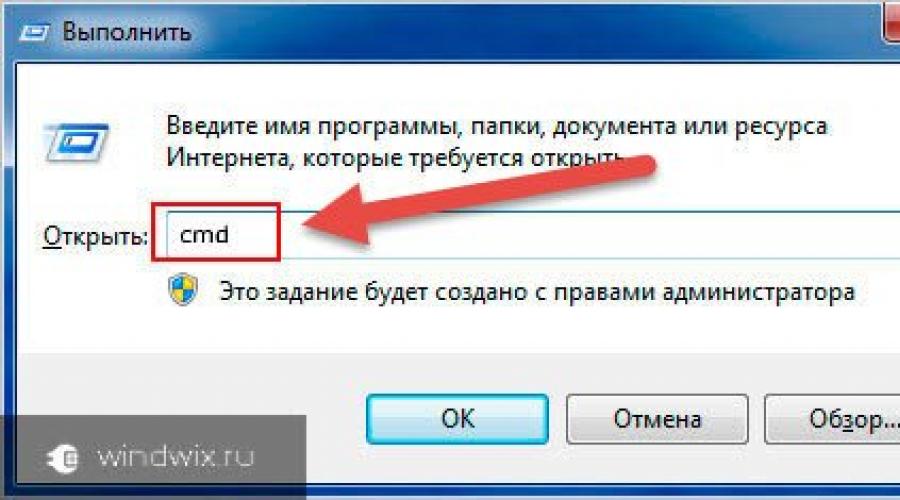
Establishing a connection( )
To establish an rdp connection, you first need to know its IP address. To do this, on the desired device, go to the command line (open "" and write " cmd»).

In the window that appears, indicate "". A list will open in which you need to find the line with the IPv4 parameter. The numbers that are indicated opposite are the data we need.

After that, on the computer from which we plan to connect, we launch the rdp client or "". To do this, you need to go to Start" and then go to " Standard».

increase
A window will open where the equipment address (IPv4) is set. Then press "".

If everything is specified as expected, a menu will appear in which you need to enter your login and password to establish a connection.

Before that, there is a choice of " Parameters”, where various rdp settings are provided:

Update( )
It is important to understand that with constant work with this tool, you need it to perform all its functions 100%. Otherwise, users may simply not achieve their goals.
For correct functioning it is necessary to specify all settings correctly. But in some cases this is not enough. It is also worthwhile to install all outgoing rdp updates from Microsoft on time. This can be done not only in the corresponding center provided in the operating system itself, but also on the developer's official page.
Changing the RDP port( )
For standard connection to remote computer port 3389 is used. In this case, the interaction occurs through TCP protocol. Therefore it is used without udp.
To increase the security of the connection, it is possible to change the RDP port. Changing the value will reduce the risk of intrusion into the system in case of automated selection of passwords.
For the procedure, you must use the registry editor:

No connection( )
Sometimes users may encounter a situation where rdp is not working. It is important to note that, judging by the statistics, the user still manages to get to the server, but some network tools do not let him go further. There are several effective ways to solve this problem.
As with past client versions of Microsoft operating systems, users of Pro and Enterprise Windows 10 (but not Home) editions can remotely connect to their computers through Remote Desktop Services (RDP). However, there is a limit on the number of simultaneous RDP sessions - only one remote user can work at the same time. When trying to open a second RDP session, the session of the first user is prompted to terminate.
IN English version the warning is:
Another user is signed in. If you continue, they'll be disconnected. Do you want to sign anyway?
The fact is that in desktop editions of Microsoft operating systems there are the following main restrictions on using the Remote Desktop service:
- Support for RDP access is available only in older editions of Windows (Professional and higher), and in home editions (Home) this functionality is disabled.
- Only one remote RDP connection is possible. When trying to open a second RDP session, the user is prompted to terminate the existing connection.
- In the event that there is a user working at the computer console (locally), when RDP connects remotely, his session will be disconnected (blocked). The converse statement is also correct: the remote RDP session is forcibly terminated if the user logs in on the system console
In fact, the limit on the number of simultaneous rdp connections is not technical, but rather licensed, prohibiting the creation of workstation-based terminal RDP server for multiple users. Although from a technical point of view, any edition of Windows, if there is enough memory, can support the simultaneous operation of several dozen remote users (on average, 150-200 MB of memory is required per user session, excluding running applications). Those. the maximum number of simultaneous sessions is in theory limited only by computer resources.
We will look at two ways to disable the limit on the number of simultaneous RDP connections in Windows 10:
Important. Initially, in the very first version of the article, the main working option to remove the limit on the number of simultaneous RDP user connections was the method of modifying and replacing the file termsrv.dll in the %SystemRoot%\System32 folder. However, when you install a new build of Windows 10 or some security updates, this file is updated. As a result, you have to edit this Hex file every time with an editor, which is quite tedious. Therefore, as the main way to organize a free terminal server on client Windows 10, it is worth considering the utility RDP Wrapper Library.
Note. System modifications described in this article are likely to be considered a violation of the Windows license agreement with all the ensuing consequences.
RDP Wrapper Library
An alternative to modifying the termsrv.dll file is to use the project RDP Wrapper Library. This program works as a layer between the Service Control Manager (SCM-Service Control Manager) and Terminal Services (Terminal Services) and allows you to enable not only support for multiple simultaneous RDP sessions, but also activate support for RDP Host on home editions of Windows 10. RDP Wrapper does not makes no changes to the termsrv.dll file, just loading termsrv with modified parameters.
Thus, this solution will work even if you update the version of the termsrv.dll file, which allows you not to be afraid of Windows updates.
Important. Before installing RDP Wrapper: It is important that you use the original (unpatched) version of the termsrv.dll file. Otherwise, RDP Wrapper may not work stably, or not start at all.
You can download the RDP Wrapper from the GitHub repository: https://github.com/binarymaster/rdpwrap/releases (latest available version RDP Wrapper Library v1.6.2 was released relatively recently - December 28, 2017). Judging by the information on the developer's page, all versions of Windows are supported. Windows 10 is supported up to Insider Preview build 10.0.17063.1000 on December 13, 2017.
Advice. By the way, the RDP Wrapper Library sources are available, which allows you to build executable files yourself if you wish.
The RDPWrap-v1.6.2.zip archive contains several files:
- RDPWinst.exe - RDP Wrapper Library installer/uninstaller
- RDPConf.exe - RDP Wrapper configuration utility
- RDPCheck.exe - Local RDP Checker - RDP check utility
- install.bat, uninstall.bat, update.bat - batch files for installing, uninstalling and updating RDP Wrapper

To install the utility, run the install.bat file with administrator rights.

After installation is complete, run RDPConfig.exe. And make sure that in the section diagnostics all elements are colored green.
Note. In my case, because there is no Internet access on the computer, the program could not get the current version of the INI file from Github with settings for my version of Windows. Therefore, the status is indicated. Download the rdpwrap.ini file from the development resource and place it in the installation directory. Restart the service and make sure the label changes to .

Of the interesting features of the new version of RDP Wrapper:
- option Hideusersonlogonscreen- allows .
- When the option is disabled single session per user- several simultaneous RDP sessions under one account will be allowed (the registry key is set fSingleSessionPerUser= 0 in the branch HKLM\SYSTEM\ CurrentControlSet\Control\Terminal Server\fSingleSessionPerUser).
In the event that after updating the version of Windows, RDP Wrapper does not work, check that there is an inscription in the Diagnostics section.

Try updating the ini file with a script update.bat, or manually and reinstall the service
rdpwinst.exe -u
rdpwinst.exe -i
We are trying to open a second RDP session. Everything worked out! Now our Windows 10 allows you to simultaneously connect via RDP to two remote users at once.
 The utility should work on all currently supported editions of Windows: Windows Vista, Windows 7, Windows 8, Windows 8.1 and Windows 10. Thus, you can make a terminal server from any client version of Windows.
The utility should work on all currently supported editions of Windows: Windows Vista, Windows 7, Windows 8, Windows 8.1 and Windows 10. Thus, you can make a terminal server from any client version of Windows.
Modifying the termsrv.dll file
Note. This method applicable only to the RTM version of Windows 10 x64 (10240).
You can remove the limit on the number of RDP connections by modifying the termsrv.dll file (a library file used by Remote Desktop Services). The file is located in the C:\Windows\System32 directory).
Before modifying the termsrv.dll file, it is advisable to create a backup copy of it (if necessary, you can return to the original version of the file):
copy c:\Windows\System32\termsrv.dll termsrv.dll_backup
 Before editing the termsrv.dll file, you need to become its owner and give the administrators group full rights to it (all operations are performed in the same way as described in the article). Then stop the Remote Desktop service (TermService) from the services.msc console or from the command line:
Before editing the termsrv.dll file, you need to become its owner and give the administrators group full rights to it (all operations are performed in the same way as described in the article). Then stop the Remote Desktop service (TermService) from the services.msc console or from the command line:
Net stop TermService
 For Windows 10 x64 RTM edition (termsrv.dll file version is 10.0.10240.16384): Open the termsrv.dll file with any HEX editor (for example, Tiny Hexer)
For Windows 10 x64 RTM edition (termsrv.dll file version is 10.0.10240.16384): Open the termsrv.dll file with any HEX editor (for example, Tiny Hexer)
Find the line:
39 81 3C 06 00 00 0F 84 73 42 02 00
And replace it with:
B8 00 01 00 00 89 81 38 06 00 00 90
 Save the file and start the TermService service.
Save the file and start the TermService service.
Fixing RDP flaws with the RDP Wrapper Library
Microsoft desktop operating systems have some limitations when it comes to Remote Desktop Services. So, firstly, support for the server part (RDP Host) is only available in older editions of Windows (not lower than Professional). In home editions, this functionality is disabled, so connect to younger Windows versions over RDP is not possible.
And secondly, the number of parallel RDP sessions is limited. Only one simultaneous connection via RDP is allowed, and when you try to open a second RDP session, the system will display a message stating that there is already one user in the system and prompt him to throw it out to end his session.
Bypassing these limitations will allow the project RDP Wrapper Library by Stas'M. The RDP Wrapper works as a layer between the Service Control Manager (SCM) and the Remote Desktop Service. At the same time, unlike other solutions of this kind, it does not change the file termsrv.dll(library used by Remote Desktop Services) so you don't have to worry about Windows updates.