»
How can a php programmer make good money at home?
Most successful php programmers make good money from home. At the beginning of any earnings there are difficulties. It happens that difficulties and lack of knowledge of earning methods discourage all the desire to earn money at home, and then programmers are looking for an opportunity to work in offices, where there is a big guarantee that money can be received every month, and professional growth is possible.
But being able to work from home has more pros than cons.
pros
You will work for yourself. No one will fire you, you can distribute your own schedule or work at the time you want.
You yourself choose for yourself a way to earn money with the help of programming, which, firstly, will increase your interest in work, and secondly, you have great freedom of action. You don't have to work on what you don't like. There are also more opportunities to combine ways of earning.
Minuses
At first it will be difficult, and in order to get the first money for your work, you need to invest a lot of effort and time. And for profit to always be necessary to constantly develop and have patience and correctly distribute your schedule yourself so that you have enough time to complete the work on time.
Earnings on your scripts
There are many different scripts on the Internet that people can easily download and install on their site. You can write your own unique script, and there are two options for how you can earn money from your script. Sell it or place it through file sharing. You can also use two options. For example, light scripts, but at the same time, it is also very important to place exactly those scripts through file sharing that will be in great demand. For this, scripts must be in demand so that people download for their needs.
Large scripts can be sold for reasonable prices. You can place an ad on the forums, or if you have your own personal blog or website, place ads to sell scripts.
In any case, whichever option you choose, place the script in the archive and be sure to include detailed instructions and contact information about yourself. Be sure to give support, because it is important for your work for yourself. After all, you need to be recommended or your scripts downloaded. They must be of high quality. If a person asked you for help, politely explain to him about the script or help him install it. Your scripts should have comments. What each function is responsible for, etc. After all, a person can easily get confused in your code, where there will be no notation.
Own and joint projects
It is good for successful earnings to create your own website. There are many opportunities to make money with your website. If you promote it well, then you can place scripts for sale there. Collaborative projects will expand your opportunities, which is good for the success of programming at home. Therefore, look for partners or do not refuse offers to create a project together.
On your site, you should definitely add features that attract attention. The site may have the usual simple look, but at the same time with its own twist. A personal website contributes to an increase in customers. They will see how your scripts work if they do not take too long to load, they are interesting to use, and most importantly original, they do not look like anything. Then you will be successful.
Earnings on orders
To do this, it is enough to register in various exchanges for freelancers and look for orders. Showcase your portfolio of work. But be careful, there are not honest people in the world and so that you don’t fall for deception, first show the work that is located on your server (by the way, in this case you will need to rent a vps http://nkvd.pro/vps/), and then if you are paid a part, then transfer half to their server, and with the second part. This method of earning is considered profitable, but depends on the degree of your knowledge and skills. It also depends on the feedback from your customers. To succeed in this way of earning, do the work honestly and efficiently. You must be able to communicate with customers, clearly explain what you know and what you don't.
This is not the whole list of php programmer earnings, but thanks to these ways of earning, which are written above, you can already earn money without leaving your home. At the initial stage, this will be a great achievement. The main thing is not to stop there. Constantly improve and create projects that will bring you not only good income, but also pleasure.
about the author
How can a php programmer make good money at home?
With the advent of computers and the Internet, many additional professions have appeared.
Programming specialists are now in demand, because many different projects are launched via the Internet. Therefore, all applicants should think about choosing a specialty related to computers.
How to make money on knowledge of PHP? In this article we will consider one of the areas of programming. The scripting language is actively used for application development.
The technology has been relevant for many years, and if you learn PHP, you can get good money. Most importantly, the demand for specialists in this field is huge.
How much does a PHP programmer earn?
It is impossible to name the exact amount, because everyone works in different companies, and some even work at home. In any case, active workers receive a good salary.
Those who work from the comfort of their homes receive exactly as much as they have time to complete orders. Prices in a niche are rarely set, most often they are negotiated individually.
Of the advantages of working as a PHP programmer, it is worth noting the serious prospects and relevance of the activity. At a time when the Internet penetrates almost all areas, it is really profitable to work as a programmer.
Well:
"Earnings on your own service by e-mail newsletters"
. Draining a closed pool for 33 thousand rubles. Warehouse reviews vary. Based on the reviews, the course is not suitable for everyone, but only for those who have already encountered similar courses or mailing lists. Material sent anonymous userwith comment:
« I'm leaking this course because I was banned at the warehouse just like that. At the rate I will say one thing that is suitable for small mailings. Beginners will not understand anything, but they can look for familiarization. The reviews are different, I refrained from commenting. If you want to learn how to send out mass letters, go to Shelest, he will help you. I studied with him, and I bought this course only for general development. I hope someone will be useful.» Material can be removed at the request of the copyright holder!
Evaluate
Course Description:
A unique author's course of video lessons Quick start technology in email newsletters - How to send email letters in large volumes to "potential" customers. With the advent of the trend to develop business through the Internet and the constant increase in the number of active Internet users, various training courses began to appear, both for beginners and advanced users. This course is intended for everyone who is interested in how to effectively get traffic and sales without spending huge amounts on it. The most effective and convenient tool for online sales is the promotion of services and goods using e-mail (e-mail marketing).
To organize professional e-mail marketing, and not just mass mailing, you need to develop a systematic approach, collect a subscriber base, automate this process to increase stable profits, generate statistics and other tasks that are difficult to complete without professional help. In this course, as a quick start technology in email newsletters, it is proposed to send letters via VDS servers. Why pay big money for mailing services if you can set it up yourself? And get the opportunity to send anyone, anything in large volumes of letters to your customers. This course will help you set up a VDS server to automatically send emails and create professional e-mail marketing, while any user can complete the setup by simply following the step-by-step instructions from the author's video course. Cool tools of excellence! The beauty of SET is that it is written in Python and does not require any third-party Python modules that would have to be installed additionally. The work is carried out through an interactive menu, where you only need to select the desired items for the application to work. At each step, the menu is accompanied by a good description of the proposed subpoints, so even a child can handle it (it gets a little scary here) But in some situations it is simply necessary to tune the toolkit itself, and for this you will have to turn to the settings file.
What you will learn from the course:
- Setting up vds for email newsletters
- How to bypass spam filters. Reasons why emails end up in spam
- How to quickly and easily uniqueize emails
- How to collect 100% working and live e-mail addresses, and not just addresses, but e-mail
- addresses of your target audience
- How to work with SMTP and how to raise an SMTP server
- Get all the software you need
- How to make money by sending letters, what affiliate programs to work with
- Template generation with its subsequent upload to the VDS server(s)
- Extract email, scan inurl (readme.txt)
- Creating databases - cleaning, splitting, deleting email duplicates
Any search for vulnerabilities on web resources begins with reconnaissance and information gathering.
Intelligence can be either active - brute force of files and directories of the site, launching vulnerability scanners, manually viewing the site, or passive - searching for information in different search engines. Sometimes it happens that a vulnerability becomes known even before the opening of the first page of the site.
How is this possible?
Search robots, constantly roaming the Internet, in addition to information useful to the average user, often fix what can be used by attackers when attacking a web resource. For example, script errors and files with sensitive information (from configuration files and logs to files with authentication data and database backups).
From the point of view of a search robot, an sql query execution error message is a plain text, inseparable, for example, from the description of the goods on the page. If suddenly the search robot stumbles upon a file with the .sql extension, which for some reason ended up in the working folder of the site, then it will be perceived as part of the site's content and will also be indexed (including, possibly, the passwords specified in it).
Such information can be found by knowing strong, often unique, keywords that help separate "vulnerable pages" from pages that do not contain vulnerabilities.
A huge database of special queries using keywords (so-called dorks) exists at exploit-db.com and is known as the Google Hack Database.
Why google?
Dorks are targeted primarily at google for two reasons:
− the most flexible syntax for keywords (given in Table 1) and special characters (given in Table 2);
- the google index is still more complete than that of other search engines;
Table 1 - Key google keywords
Keyword
|
Meaning
|
Example
|
site
|
Search only on the specified site. Considers only url
|
site:somesite.ru - finds all pages on the given domain and subdomains
|
inurl
|
Search by words present in uri. Unlike cl. words “site”, searches for matches after the site name
|
inurl:news - finds all pages where the given word occurs in the uri
|
intext
|
Search in the body of the page
|
intext:"traffic" - completely similar to the usual query "traffic"
|
title
|
Search in the title of the page. Text between tags <br></td>
<td width="214">intitle:”index of” - finds all pages with a directory listing <br></td>
</tr><tr><td width="214">ext <br></td>
<td width="214">Search for pages with the specified extension <br></td>
<td width="214">ext:pdf - finds all pdf files <br></td>
</tr><tr><td width="214">filetype <br></td>
<td width="214">At present, it is completely analogous to class. the word "ext" <br></td>
<td width="214">filetype:pdf - similar <br></td>
</tr><tr><td width="214">related <br></td>
<td width="214">Search for sites with similar topics <br></td>
<td width="214">related:google.ru - will show its analogues <br></td>
</tr><tr><td width="214">link <br></td>
<td width="214">Search for sites that link to this <br></td>
<td width="214">link:somesite.ru - finds all sites that have a link to this <br></td>
</tr><tr><td width="214">define <br></td>
<td width="214">Show word definition <br></td>
<td width="214">define:0day - definition of the term <br></td>
</tr><tr><td width="214">cache <br></td>
<td width="214">Show cached page content (if available) <br></td>
<td width="214">cache:google.com - open page from cache <br></td>
</tr></tbody></table><p>Table 2 - Google Query Special Characters <br></p><table><tbody><tr><td width="214"><b>Symbol</b><br></td>
<td width="214"><b>Meaning</b><br></td>
<td width="214"><b>Example</b><br></td>
</tr><tr><td width="214">“<br></td>
<td width="214">Exact Phrase <br></td>
<td width="214">intitle:"RouterOS router configuration page" - search for routers <br></td>
</tr><tr><td width="214">*<br></td>
<td width="214">Any text <br></td>
<td width="214">inurl:"bitrix*mcart" - search for sites on bitrix with a vulnerable mcart module <br></td>
</tr><tr><td width="214">.<br></td>
<td width="214">Any character <br></td>
<td width="214">Index.of - similar to the index of query <br></td>
</tr><tr><td width="214">-<br></td>
<td width="214">Delete word <br></td>
<td width="214">error -warning - show all pages with error but no warning <br></td>
</tr><tr><td width="214">..<br></td>
<td width="214">Range <br></td>
<td width="214">cve 2006..2016 - show vulnerabilities by year starting from 2006 <br></td>
</tr><tr><td width="214">|<br></td>
<td width="214">Logical "or" <br></td>
<td width="214">linux | windows - show pages where either the first or second word occurs <br></td>
</tr></tbody></table><br>It should be understood that any request to a search engine is a search only by words. <br>It is useless to look for meta-characters on the page (quotes, brackets, punctuation marks, etc.). Even searching for an exact phrase in quotation marks is a word search, followed by an exact match already in the results. <p>All Google Hack Database dorks are logically divided into 14 categories and are presented in Table 3. <br>Table 3 - Google Hack Database Categories <br></p><table><tbody><tr><td width="168"><b>Category</b><br></td>
<td width="190"><b>What makes it possible to find</b><br></td>
<td width="284"><b>Example</b><br></td>
</tr><tr><td width="168">footholds <br></td>
<td width="190">Web shells, public file managers <br></td>
<td width="284">Find all hacked sites containing the listed webshells: <br>(intitle:"phpshell" OR intitle:"c99shell" OR intitle:"r57shell" OR intitle:"PHP Shell" OR intitle:"phpRemoteView") `rwx` "uname" <br></td>
</tr><tr><td width="168">Files containing usernames <br></td>
<td width="190">Registry files, configuration files, logs, files containing the history of entered commands <br></td>
<td width="284">Find all registry files containing account information: <br><i>filetype:reg reg +intext:"internet account manager"</i><br></td>
</tr><tr><td width="168">Sensitive Directories <br></td>
<td width="190">Directories with various information (personal documents, vpn configs, hidden repositories, etc.) <br></td>
<td width="284">Find all directory listings containing files related to vpn: <br><i>"Config" intitle:"Index of" intext:vpn</i><br>Sites containing git repositories: <br><i>(intext:"index of /.git") ("parent directory")</i><br></td>
</tr><tr><td width="168">Web Server Detection <br></td>
<td width="190">Version and other information about the web server <br></td>
<td width="284">Find the administrative consoles of the JBoss server: <br><i>inurl:"/web-console/" intitle:"Administration Console"</i><br></td>
</tr><tr><td width="168">Vulnerable Files <br></td>
<td width="190">Scripts containing known vulnerabilities <br></td>
<td width="284">Find sites that use a script that allows you to upload an arbitrary file from the server: <br><i>allinurl:forcedownload.php?file=</i><br></td>
</tr><tr><td width="168">Vulnerable Servers <br></td>
<td width="190">Installation scripts, web shells, open administrative consoles, etc. <br></td>
<td width="284">Find open PHPMyAdmin consoles run as root: <br><i>intitle:phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root@*"</i><br></td>
</tr><tr><td width="168">error messages <br></td>
<td width="190">Various errors and warnings often reveal important information - ranging from CMS version to passwords <br></td>
<td width="284">Sites with errors in executing sql queries to the database: <br><i>"Warning: mysql_query()" "invalid query"</i><br></td>
</tr><tr><td width="168">Files containing juicy info <br></td>
<td width="190">Certificates, backups, emails, logs, sql scripts, etc. <br></td>
<td width="284">Find initialization sql scripts: <br><i>filetype:sql and "insert into" -site:github.com</i><br></td>
</tr><tr><td width="168">Files containing passwords <br></td>
<td width="190">Everything that can contain passwords - logs, sql scripts, etc. <br></td>
<td width="284">Logs mentioning passwords: <br><i>filetype:</i><i>log</i><i>intext:</i><i>password |</i><i>pass |</i><i>pw</i><br>sql scripts containing passwords: <br><i>ext:</i><i>sql</i><i>intext:</i><i>username</i><i>intext:</i><i>password</i><br></td>
</tr><tr><td width="168">Sensitive Online Shopping Info <br></td>
<td width="190">Information related to online shopping <br></td>
<td width="284">Find pincodes: <br><i>dcid=</i><i>bn=</i><i>pin</i><i>code=</i><br></td>
</tr><tr><td width="168">Network or vulnerability data <br></td>
<td width="190">Information that is not directly related to the web resource, but affects the network or other non-web services <br></td>
<td width="284">Find automatic proxy configuration scripts containing information about the internal network: <br><i>inurl:proxy | inurl:wpad ext:pac | ext:dat findproxyforurl</i><br></td>
</tr><tr><td width="168">Pages containing portals <br></td>
<td width="190">Pages containing login forms <br></td>
<td width="284">saplogon webpages: <br><i>intext:"2016 SAP AG. All rights reserved.” intitle:"login"</i><br></td>
</tr><tr><td width="168">Various Online Devices <br></td>
<td width="190">Printers, routers, monitoring systems, etc. <br></td>
<td width="284">Find the printer configuration panel: <br><i>title:"</i><i>hp</i><i>laserjet"</i><i>inurl:</i><i>SSI/</i><i>Auth/</i><i>set_</i><i>config_</i><i>deviceinfo.</i><i>htm</i><br></td>
</tr><tr><td width="168">Advisories and Vulnerabilities <br></td>
<td width="190">Sites on vulnerable versions of CMS <br></td>
<td width="284">Find vulnerable plugins through which you can upload an arbitrary file to the server: <br><i>inurl:fckeditor -intext:"ConfigIsEnabled = False" intext:ConfigIsEnabled</i><br></td>
</tr></tbody></table><br>Dorks are more often focused on searching all sites on the Internet. But nothing prevents you from limiting the search area on any site or sites. <br>Each request to google can be focused on a specific site by adding the keyword "site:somesite.com" to the request. This keyword can be appended to any dork. <p><b>Vulnerability Search Automation</b><br>So the idea was born to write a simple utility that automates the search for vulnerabilities using a search engine (google) and based on the Google Hack Database.</p><p>The utility is a script written in nodejs using phantomjs. To be precise, the script is interpreted by phantomjs itself. <br>Phantomjs is a full-fledged web browser without a graphical interface, driven by js code and with a convenient API. <br>The utility received a quite understandable name - dorks. By running it on the command line (without options), we get a short help with several examples of use: <br><br><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/edd/6fb/ccc/edd6fbccc5ec340abe750f3073c1b427.jpg' width="100%" loading=lazy loading=lazy><br>Figure 1 - List of basic dorks options</p><p>The general syntax of the utility is: dork "command" "list of options". <br>A detailed description of all options is presented in Table 4.</p><p>Table 4 - Syntax dorks <br></p><table border="1"><tbody><tr><td width="214"><b>Team</b><br></td>
<td width="214"><b>Option</b><br></td>
<td width="214"><b>Description</b><br></td>
</tr><tr><td rowspan="4" width="214">ghdb <br></td>
<td width="214">-l <br></td>
<td width="214">Display numbered list of dork categories Google Hack Database <br></td>
</tr><tr><td width="214">-c "category number or name" <br></td>
<td width="214">Download dorks of the specified category by number or name <br></td>
</tr><tr><td width="214">-q "phrase" <br></td>
<td width="214">Download dorks found on request <br></td>
</tr><tr><td width="214">-o "file" <br></td>
<td width="214">Save result to file (only with -c|-q options) <br></td>
</tr><tr><td rowspan="8" width="214">google <br></td>
<td width="214">-d "dork" <br></td>
<td width="214">Specify arbitrary dork (option can be used many times, combination with -D option is allowed) <br></td>
</tr><tr><td width="214">-D "file" <br></td>
<td width="214">Use dorks from a file <br></td>
</tr><tr><td width="214">-s "site" <br></td>
<td width="214">Set site (option can be used multiple times, combination with -S option is allowed) <br></td>
</tr><tr><td width="214">-S "file" <br></td>
<td width="214">Use sites from a file (dorks will be searched for each site independently) <br></td>
</tr><tr><td width="214">-f "filter" <br></td>
<td width="214">Set additional keywords (will be added to each dork) <br></td>
</tr><tr><td width="214">-t "number of ms" <br></td>
<td width="214">Interval between requests to google <br></td>
</tr><tr><td width="214">-T "number of ms" <br></td>
<td width="214">Timeout if captcha encountered <br></td>
</tr><tr><td width="214">-o "file" <br></td>
<td width="214">Save the result to a file (only those dorks for which something was found will be saved) <br></td>
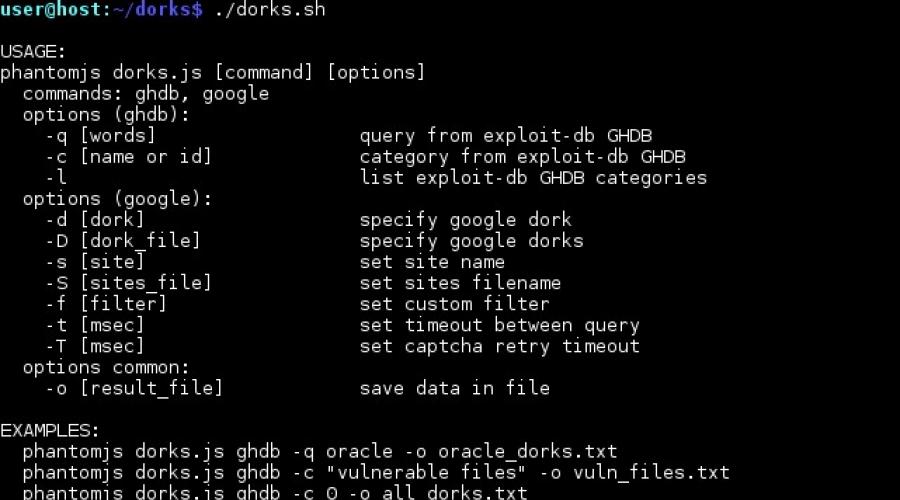
</tr></tbody></table><br>Using the ghdb command, you can get all the dorks from exploit-db on an arbitrary request, or specify the entire category. If you specify category 0, then the entire database will be unloaded (about 4.5 thousand dorks). <p>The list of categories currently available is shown in Figure 2. <br><br><img src='https://i2.wp.com/habrastorage.org/getpro/habr/post_images/b8f/b11/ffe/b8fb11ffeaced5066fd2fd9e43be67fb.jpg' width="100%" loading=lazy loading=lazy></p><p>Figure 2 - List of available categories of GHDB dorks</p><p>The google team will substitute each dork into the google search engine and analyze the result for matches. Dorks for which something was found will be saved to a file. <br>The utility supports different search modes: <br>1 dork and 1 site; <br>1 dork and many sites; <br>1 site and many dorks; <br>many sites and many dorks; <br>The list of dorks and sites can be specified both through an argument and through a file.</p><p><b>Demonstration of work</b><br>Let's try to look for any vulnerabilities using the example of searching for error messages. The command: dorks ghdb –c 7 –o errors.dorks will load all known dorks of the “Error Messages” category as shown in Figure 3. <br><br><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/28c/386/641/28c386641d1528652f7f8e8b8089097a.jpg' width="100%" loading=lazy loading=lazy><br>Figure 3 - Loading all known dorks of the “Error Messages” category</p><p>Dorks loaded and saved to a file. Now it remains to "set" them on some site (see Figure 4). <br><br><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/8e0/a8a/3af/8e0a8a3af4f26544da1faa584813dbff.jpg' width="100%" loading=lazy loading=lazy><br>Figure 4 - Search for vulnerabilities of the site of interest in the google cache</p><p>After some time, several pages containing errors are found on the site under study (see Figure 5).</p><p><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/10b/e83/ba3/10be83ba38f172213ba06b3f9ad05a58.jpg' width="100%" loading=lazy loading=lazy><br>Figure 5 - Found error messages</p><p>As a result, in the result.txt file we get the complete list of dorks that lead to the error. <br>Figure 6 shows the result of searching for site errors. <br><br>Figure 6 - The result of the search for errors</p><p>In the cache for this dork, a full backtrace is displayed, revealing the absolute paths of the scripts, the content management system of the site, and the type of database (see Figure 7). <br><br><img src='https://i2.wp.com/habrastorage.org/getpro/habr/post_images/0a9/455/588/0a9455588496d6609f5e13d598cb5a48.jpg' width="100%" loading=lazy loading=lazy><br>Figure 7 - disclosure of information about the site structure</p><p>However, it should be borne in mind that not all dorks from GHDB give a true result. Also, google may not find an exact match and show a similar result.</p><p>In this case, it is wiser to use your personal list of dorks. For example, it is always worth looking for files with “unusual” extensions, examples of which are shown in Figure 8. <br><br><img src='https://i2.wp.com/habrastorage.org/getpro/habr/post_images/d7f/865/693/d7f865693f7fcf13137598eeed0ecb58.jpg' width="100%" loading=lazy loading=lazy><br>Figure 8 - List of file extensions that are not typical for a regular web resource</p><p>As a result, at the command dorks google -D extensions.txt -f bank, from the very first request, google starts returning sites with "unusual" file extensions (see Figure 9). <br><br><img src='https://i2.wp.com/habrastorage.org/getpro/habr/post_images/107/e1f/a2f/107e1fa2f41c4169bcc254cba2f2f4b6.jpg' width="100%" loading=lazy loading=lazy><br>Figure 9 - Search for "bad" file types on banking sites</p><p>Keep in mind that Google does not accept requests longer than 32 words.</p><p>With dorks google –d intext:”error|warning|notice|syntax” –f university <br>You can look for PHP interpreter errors on educational sites (see Figure 10). <br><br><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/717/74f/e36/71774fe3656bfc058c42d43262fdec4a.jpg' width="100%" loading=lazy loading=lazy><br>Figure 10 - Finding PHP Runtime Errors</p><p>Sometimes it is not convenient to use one or two categories of dorks. <br>For example, if you know that the site is running on the wordpress engine, then you need dorks specifically for wordpress. In this case, it is convenient to use the Google Hack Database search. dorks ghdb –q wordpress –o wordpress_dorks.txt will download all wordpress dorks, as shown in Figure 11: <br><br><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/dcb/ac9/a4e/dcbac9a4eb12f6ec775d9cccc2fdee87.jpg' width="100%" loading=lazy loading=lazy><br>Figure 11 - Search for dorks related to Wordpress</p><p>Let's go back to banks again and with the command dorks google -D wordpress_dords.txt -f bank we will try to find something interesting related to wordpress (see Figure 12). <br><br><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/042/0c2/c43/0420c2c435931704288b171f725ccc6a.jpg' width="100%" loading=lazy loading=lazy><br>Figure 12 - Searching for Wordpress vulnerabilities</p><p>It is worth noting that Google Hack Database search does not accept words shorter than 4 characters. For example, if the site's CMS is not known, but the language is known - PHP. In this case, you can filter what you need manually using the pipe and the dorks system search utility –c all | findstr /I php > php_dorks.txt (see figure 13): <br><br><img src='https://i1.wp.com/habrastorage.org/getpro/habr/post_images/4c1/2f8/6e1/4c12f86e111074293c14d6a939c6ebab.jpg' width="100%" loading=lazy loading=lazy><br>Figure 13 - Search through all dorks where there is a mention of PHP</p><p>Searching for vulnerabilities or some sensitive information in a search engine should be searched only if there is a significant index on this site. For example, if a site has 10-15 pages indexed, then it is stupid to search for something in this way. Checking the index size is easy - just enter "site:somesite.com" into the google search bar. An example of a site with an insufficient index is shown in Figure 14. <br><br><img src='https://i0.wp.com/habrastorage.org/getpro/habr/post_images/78e/1db/b4f/78e1dbb4fc78cd422cec311fc2ca9d33.jpg' width="100%" loading=lazy loading=lazy><br>Figure 14 - Checking the site index size</p><p>Now about the unpleasant... From time to time, google may request a captcha - there's nothing to be done - it will have to be entered. For example, when sorting through the “Error Messages” category (90 dorks), the captcha fell out only once.</p><p>It is worth adding that phantomjs also supports work through a proxy, both through http and through the socks interface. To enable proxy mode, uncomment the corresponding line in dorks.bat or dorks.sh.</p><p>The tool is available as source code</p>
<script>document.write("<img style='display:none;' src='//counter.yadro.ru/hit;artfast?t44.1;r"+
escape(document.referrer)+((typeof(screen)=="undefined")?"":
";s"+screen.width+"*"+screen.height+"*"+(screen.colorDepth?
screen.colorDepth:screen.pixelDepth))+";u"+escape(document.URL)+";h"+escape(document.title.substring(0,150))+
";"+Math.random()+
"border='0' width='1' height='1' loading=lazy loading=lazy>");</script>
</div>
</div>
</div>
</div>
</div>
<div class="right-rail-pseudo"></div>
<aside class="right-rail collection-sidebar">
</aside>
</div>
<div id="wide-collection-items-container"></div>
<div class="module-more-news-center">
</div>
<div class="collection-footer grid">
<aside class="right-rail collection-sidebar"></aside>
<div class="collection-footer-container">
<footer class="content-foot">
<aside class="module-social-sharing">
</aside>
<div class="content-topics">
</div>
</footer>
</div>
</div>
</article>
</main>
<footer class="footer">
<nav>
<ul class="nav">
<li>How to be on you with your PC 2023</li>
<li><a class="tracked-offpage" data-track-category="Footer" data-track-action="Go to Privacy Policy" href="">Privacy Policy</a></li>
<li><a class="tracked-offpage" data-track-category="Footer" data-track-action="Go to Contact Us" href="https://passportbdd.ru/en/feedback/">Contacts</a></li>
<li><a class="tracked-offpage" data-track-category="Footer" data-track-action="Go to Media Kit" href="">Advertising on the website</a></li>
<li><a class="tracked-offpage" data-track-category="Footer" data-track-action="Go to Sitemap" href="https://passportbdd.ru/en/sitemap.xml">Site Map</a></li>
</ul>
</nav>
</footer>
<div id="lightbox" class="lightbox">
<div class="lightbox-close"></div>
</div>
<script src="https://ajax.googleapis.com/ajax/libs/jquery/2.1.0/jquery.min.js"></script>
<script>
window.jQuery || document.write(' <
script src = "/assets/jquery.min.js" > < \/script>')
</script>
<script>
$(document).ready(function() {
var a = $(window),
b = $("body"),
c = $("#header-nav-more"),
e = c.children("a"),
f = $("#header-hamburger");
$("html").hasClass("no-touch") && (c.on("mouseenter", function() {
c.hasClass("active-hover") || c.addClass("active-hover")
}), c.on("mouseleave", function() {
c.removeClass("active-hover")
})), e.on("click", function(a) {
c.hasClass("active-hover") ? c.removeClass("active-hover") : c.addClass("active-hover"), a.preventDefault()
}), f.on("click", function() {
var a = $(this);
a.hasClass("active-hamburger") && c.removeClass("active-hover"), a.toggleClass("active-hamburger"), b.toggleClass("active-nav")
}), a.on("scroll", d(function() {
a.scrollTop() > 0 ? b.addClass("active-scroll") : b.removeClass("active-scroll")
}, 100))
});
</script>
</body>
</html><script data-cfasync="false" src="/cdn-cgi/scripts/5c5dd728/cloudflare-static/email-decode.min.js"></script> |